Requirement 5: Protect All Systems From Malicious Software
Malicious software (malware) is software or firmware designed to infiltrate or damage a computer system without the owner’s knowledge or consent, with the intent of compromising the confidentiality, integrity, or availability of the owner’s data, applications, or operating system. Examples include viruses, worms, Trojans, spyware, ransomware, keyloggers, and rootkits, malicious code, scripts, and links.
- Requirement 5: Protect All Systems From Malicious Software
- 5.1 Processes And Mechanisms For Protecting All Systems And Networks From Malicious Software Are Defined And Understood
- 5.2 Malicious Software (Malware) Is Prevented, Or Detected And Addressed
- 5.3 Anti-Malware Mechanisms And Processes Are Active, Maintained, And Monitored
- 5.4 Anti-Phishing Mechanisms Protect Users Against Phishing Attacks
- Let’s Understand With An Example
5.1 Processes And Mechanisms For Protecting All Systems And Networks From Malicious Software Are Defined And Understood
5.1.1 All security policies and operational procedures are: • Documented • Kept up to date • In use • Known to all affected parties
It is important to update policies and procedures as needed to address changes in processes, technologies, and business objectives. For this reason, consider updating these documents as soon as possible after a change occurs and not only on a periodic cycle.
5.1.2 Roles and responsibilities for performing activities are documented, assigned, and understood
Roles and responsibilities may be documented within policies and procedures or maintained within separate documents.
As part of communicating roles and responsibilities, entities can consider having personnel acknowledge their acceptance and understanding of their assigned roles and responsibilities.
5.2 Malicious Software (Malware) Is Prevented, Or Detected And Addressed
5.2.1 An anti-malware solution(s) is deployed on all system components, except for those system components identified in periodic evaluations that concludes the system components are not at risk from malware
It is beneficial for entities to be aware of “zero-day” attacks (those that exploit a previously unknown vulnerability) and consider solutions that focus on behavioral characteristics and will alert and react to unexpected behavior.
5.2.2 The deployed anti-malware solution(s): • Detects all known types of malware • Removes, blocks, or contains all known types of malware
Anti-malware solutions may include a combination of network-based controls, host-based controls, and endpoint security solutions. In addition to signature-based tools, capabilities used by modern anti-malware solutions include sandboxing, privilege escalation controls, and machine learning.
Solution techniques include preventing malware from getting into the network and removing or containing malware that does get into the network.
5.2.3 Any system components that are not at risk for malware are evaluated periodically to include the following: • A documented list of all system components not at risk for malware • Identification and evaluation of evolving malware threats for those system components • Confirmation whether such system components continue to not require anti-malware protection
If an entity determines that a particular system is not susceptible to any malware, the determination should be supported by industry evidence, vendor resources, and best practices.
The following steps can help entities during their periodic evaluations:
- Identification of all system types previously determined to not require malware protection.
- Review of industry vulnerability alerts and notices to determine if new threats exist for any identified system.
- A documented conclusion about whether the system types remain not susceptible to malware.
- A strategy to add malware protection for any system types for which malware protection has become necessary.
Trends in malware should be included in the identification of new security vulnerabilities, and methods to address new trends should be incorporated into the entity’s configuration standards and protection mechanisms as needed.
5.2.3.1 The frequency of periodic evaluations of system components identified as not at risk for malware is defined in the entity’s targeted risk analysis
Entities determine the optimum period to undertake the evaluation based on criteria such as the complexity of each entity’s environment and the number of types of systems that are required to be evaluated.
5.3 Anti-Malware Mechanisms And Processes Are Active, Maintained, And Monitored
5.3.1 The anti-malware solution(s) is kept current via automatic updates
Anti-malware mechanisms should be updated via a trusted source as soon as possible after an update is available. Using a trusted common source to distribute updates to end-user systems helps ensure the integrity and consistency of the solution architecture.
Updates may be automatically downloaded to a central location for example to allow for testing prior to being deployed to individual system components.
5.3.2 The anti-malware solution(s): • Performs periodic scans and active or real-time scans OR • Performs continuous behavioral analysis of systems or processes
Using a combination of periodic scans (scheduled and on-demand) and active, real-time (on-access) scanning helps ensure that malware residing in both static and dynamic elements of the CDE is addressed. Users should also be able to run on-demand scans on their systems if suspicious activity is detected this can be useful in the early detection of malware.
Scans should include the entire file system, including all disks, memory, and start-up files and boot records (at system restart) to detect all malware upon file execution, including any software that may be resident on a system but not currently active. Scan scope should include all systems and software in the CDE, including those that are often overlooked such as email servers, web browsers, and instant messaging software.
5.3.2.1 The frequency of scans is defined in the entity’s targeted risk analysis
Entities can determine the optimum period to undertake periodic scans based on their own assessment of the risks posed to their environments.
5.3.3 For removable electronic media, the anti-malware solution(s): • Performs automatic scans of when the media is inserted, connected, or logically mounted, OR • Performs continuous behavioral analysis of systems or processes when the media is inserted, connected, or logically mounted
Portable media devices are often overlooked as an entry method for malware. Attackers will often pre-load malware onto portable devices such as USB and flash drives; connecting an infected device to a computer then triggers the malware, introducing new threats within the environment.
5.3.4 Audit logs for the anti-malware solution(s) are enabled and retained
It is important to track the effectiveness of the anti-malware mechanisms for example, by confirming that updates and scans are being performed as expected, and that malware is identified and addressed. Audit logs also allow an entity to determine how malware entered the environment and track its activity when inside the entity’s network.
5.3.5 Anti-malware mechanisms cannot be disabled or altered by users, unless specifically documented, and authorized by management on a case-by-case basis for a limited time period
Where there is a legitimate need to temporarily disable a system’s anti-malware protection for example, to support a specific maintenance activity or investigation of a technical problem the reason for taking such action should be understood and approved by an appropriate management representative. Any disabling or altering of anti-malware mechanisms, including on administrators’ own devices, should be performed by authorized personnel. It is recognized that administrators have privileges that may allow them to disable anti-malware on their own computers, but there should be alerting mechanisms in place when such software is disabled and then follow up that occurs to ensure correct processes were followed.
5.4 Anti-Phishing Mechanisms Protect Users Against Phishing Attacks
5.4.1 Processes and automated mechanisms are in place to detect and protect personnel against phishing attacks
When developing anti-phishing controls, entities are encouraged to consider a combination of approaches. For example, using anti-spoofing controls such as Domain-based Message Authentication, Reporting & Conformance (DMARC), Sender Policy Framework (SPF), and Domain Keys Identified Mail (DKIM) will help stop phishers from spoofing the entity’s domain and impersonating personnel.
The deployment of technologies for blocking phishing emails and malware before they reach personnel, such as link scrubbers and server-side anti-malware, can reduce incidents and decrease the time required by personnel to check and report phishing attacks. Additionally, training personnel to recognize and report phishing emails can allow similar emails to be identified and permit them to be removed before being opened.
It is recommended (but not required) that anti-phishing controls are applied across an entity’s entire organization.
Let’s Understand With An Example
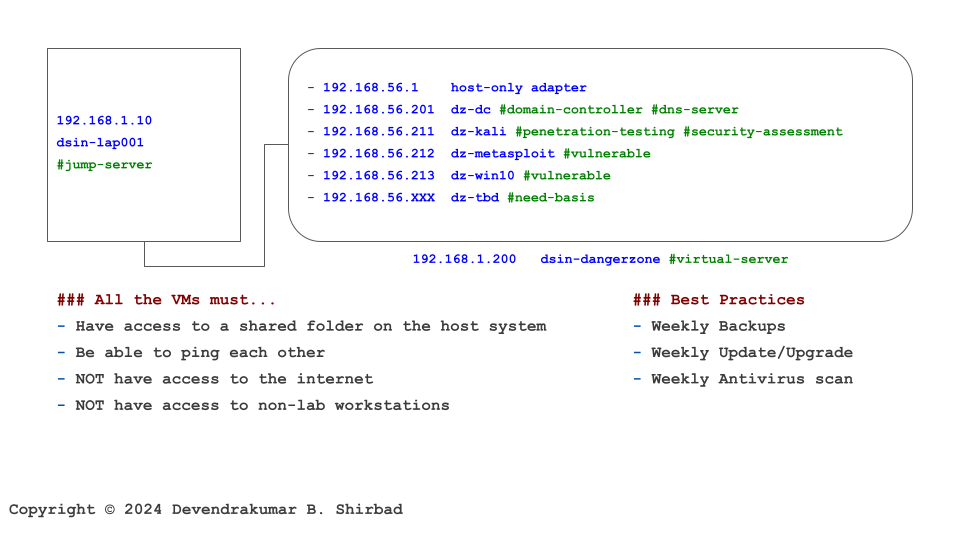
This image is borrowed from the Cybersecurity Labs. Assume it represents your work environment and cardholder data is sitting on the server dz-win10.
Requirement 5.1
It’s all about defining policies and procedures. Then, allocate the responsibilities.
Requirements 5.2 And 5.3
It suggests that the server dz-win10 should have an anti-malware solution deployed and periodic scans should be run. It doesn’t give the specifics but suggests that the solution should detect all known types of malware. It suggests some best practices e.g. frequent updates and scans, not disabling the solution etc.
Requirement 5.4
This requirement is broad. It suggests implementing anti-phishing mechanisms without any specifics. The idea here is to protect personnel against phishing attacks which are very common these days.