Requirement 9: Restrict Physical Access
Any physical access to cardholder data or systems that store, process, or transmit cardholder data provides the opportunity for individuals to access and/or remove systems or hardcopies containing cardholder data; therefore, physical access should be appropriately restricted.
- Requirement 9: Restrict Physical Access
- 9.1 Processes And Mechanisms For Restricting Physical Access To Cardholder Data Are Defined And Understood
- 9.2 Physical Access Controls Manage Entry Into Facilities And Systems Containing Cardholder Data
- 9.3 Physical Access For Personnel And Visitors Is Authorized And Managed
- 9.4 Media With Cardholder Data Is Securely Stored, Accessed, Distributed, And Destroyed
- 9.5 Point Of Interaction (POI) Devices Are Protected From Tampering And Unauthorized Substitution
- Let’s Understand With An Example
9.1 Processes And Mechanisms For Restricting Physical Access To Cardholder Data Are Defined And Understood
9.1.1 All security policies and operational procedures are: • Documented • Kept up to date • In use • Known to all affected parties
It is important to update policies and procedures as needed to address changes in processes, technologies, and business objectives. For this reason, consider updating these documents as soon as possible after a change occurs and not only on a periodic cycle.
9.1.2 Roles and responsibilities for performing activities are documented, assigned, and understood
Roles and responsibilities may be documented within policies and procedures or maintained within separate documents.
As part of communicating roles and responsibilities, entities can consider having personnel acknowledge their acceptance and understanding of their assigned roles and responsibilities.
A method to document roles and responsibilities is a responsibility assignment matrix that includes who is responsible, accountable, consulted, and informed (also called a RACI matrix).
9.2 Physical Access Controls Manage Entry Into Facilities And Systems Containing Cardholder Data
9.2.1 Appropriate facility entry controls are in place to restrict physical access to systems in the CDE
Whichever mechanism meets this requirement, it must be sufficient for the organization to verify that only authorized personnel are granted access.
9.2.1.1 Individual physical access to sensitive areas within the CDE is monitored with either video cameras or physical access control mechanisms (or both) as follows: • Entry and exit points to/from sensitive areas within the CDE are monitored • Monitoring devices or mechanisms are protected from tampering or disabling • Collected data is reviewed and correlated with other entries • Collected data is stored for at least three months, unless otherwise restricted by law
Whichever mechanism meets this requirement, it should effectively monitor all entry and exit points to sensitive areas.
Criminals attempting to gain physical access to sensitive areas will often try to disable or bypass the monitoring controls. To protect these controls from tampering, video cameras could be positioned so they are out of reach and/or be monitored to detect tampering. Similarly, physical access control mechanisms could be monitored or have physical protections installed to prevent them from being damaged or disabled by malicious individuals.
9.2.2 Physical and/or logical controls are implemented to restrict use of publicly accessible network jacks within the facility
Whether logical or physical controls, or a combination of both, are used, they should prevent an individual or device that is not explicitly authorized from being able to connect to the network.
9.2.3 Physical access to wireless access points, gateways, networking/communications hardware, and telecommunication lines within the facility is restricted
Without appropriate physical security over access to wireless components and devices, and computer networking and telecommunications equipment and lines, malicious users could gain access to the entity’s network resources. Additionally, they could connect their own devices to the network to gain unauthorized access to the CDE or systems connected to the CDE.
Additionally, securing networking and communications hardware prevents malicious users from intercepting network traffic or physically connecting their own devices to wired network resources.
9.2.4 Access to consoles in sensitive areas is restricted via locking when not in use
Locking console login screens prevents unauthorized persons from gaining access to sensitive information, altering system configurations, introducing vulnerabilities into the network, or destroying records.
9.3 Physical Access For Personnel And Visitors Is Authorized And Managed
9.3.1 Procedures are implemented for authorizing and managing physical access of personnel to the CDE, including: • Identifying personnel • Managing changes to an individual’s physical access requirements • Revoking or terminating personnel identification • Limiting access to the identification process or system to authorized personnel
It is important to visually identify the personnel that are physically present, and whether the individual is a visitor or an employee.
9.3.1.1 Physical access to sensitive areas within the CDE for personnel is controlled as follows: • Access is authorized and based on individual job function • Access is revoked immediately upon termination • All physical access mechanisms, such as keys, access cards, etc., are returned or disabled upon termination
Where possible, organizations should have policies and procedures to ensure that before personnel leaving the organization, all physical access mechanisms are returned, or disabled as soon as possible upon their departure. This will ensure personnel cannot gain physical access to sensitive areas once their employment has ended.
9.3.2 Procedures are implemented for authorizing and managing visitor access to the CDE, including: • Visitors are authorized before entering • Visitors are escorted at all times • Visitors are clearly identified and given a badge or other identification that expires • Visitor badges or other identification visibly distinguishes visitors from personnel
Visitor controls are important to reduce the ability of unauthorized and malicious persons to gain access to facilities and potentially to cardholder data.
Visitor controls ensure visitors are identifiable as visitors so personnel can monitor their activities, and that their access is restricted to just the duration of their legitimate visit.
9.3.3 Visitor badges or identification are surrendered or deactivated before visitors leave the facility or at the date of expiration
Ensuring that visitor badges are returned or deactivated upon expiry or completion of the visit prevents malicious persons from using a previously authorized pass to gain physical access into the building after the visit has ended.
9.3.4 A visitor log is used to maintain a physical record of visitor activity within the facility and within sensitive areas, including: • The visitor’s name and the organization represented • The date and time of the visit • The name of the personnel authorizing physical access • Retaining the log for at least three months, unless otherwise restricted by law
When logging the date and time of visit, including both in and out times is considered a best practice, since it provides helpful tracking information and provides assurance that a visitor has left at the end of the day. It is also good to verify that a visitor’s ID (driver’s license, etc.) matches the name they put on the visitor log.
9.4 Media With Cardholder Data Is Securely Stored, Accessed, Distributed, And Destroyed
9.4.1 All media with cardholder data is physically secured
Controls for physically securing media are intended to prevent unauthorized persons from gaining access to cardholder data on any media. Cardholder data is susceptible to unauthorized viewing, copying, or scanning if it is unprotected while it is on removable or portable media, printed out, or left on someone’s desk.
9.4.1.1 Offline media backups with cardholder data are stored in a secure location
For secure storage of backup media, a good practice is to store media in an off-site facility, such as an alternate or backup site or commercial storage facility.
9.4.1.2 The security of the offline media backup location(s) with cardholder data is reviewed at least once every 12 months
Conducting regular reviews of the storage facility enables the organization to address identified security issues promptly, minimizing the potential risk. It is important for the entity to be aware of the security of the area where media is being stored.
9.4.2 All media with cardholder data is classified in accordance with the sensitivity of the data
It is important that media be identified such that its classification status is apparent. This does not mean however that the media needs to have a “confidential” label.
9.4.3 Media with cardholder data sent outside the facility is secured as follows: • Media sent outside the facility is logged • Media is sent by secured courier or other delivery method that can be accurately tracked • Offsite tracking logs include details about media location
Media may be lost or stolen if sent via a non-trackable method such as regular postal mail. The use of secure couriers to deliver any media that contains cardholder data allows organizations to use their tracking systems to maintain inventory and location of shipments.
9.4.4 Management approves all media with cardholder data that is moved outside the facility (including when media is distributed to individuals)
Without a firm process for ensuring that all media movements are approved before the media is removed from secure areas, the media would not be tracked or appropriately protected, and its location would be unknown, leading to lost or stolen media.
9.4.5 Inventory logs of all electronic media with cardholder data are maintained
Without careful inventory methods and storage controls, stolen or missing electronic media could go unnoticed for an indefinite amount of time.
9.4.5.1 Inventories of electronic media with cardholder data are conducted at least once every 12 months
Without careful inventory methods and storage controls, stolen or missing electronic media could go unnoticed for an indefinite amount of time.
9.4.6 Hard-copy materials with cardholder data are destroyed when no longer needed for business or legal reasons, as follows: • Materials are cross-cut shredded, incinerated, or pulped so that cardholder data cannot be reconstructed • Materials are stored in secure storage containers prior to destruction
Consider “to-be-shredded” containers with a lock that prevents access to its contents or that physically prevent access to the inside of the container.
9.4.7 Electronic media with cardholder data is destroyed when no longer needed for business or legal reasons via one of the following: • The electronic media is destroyed • The cardholder data is rendered unrecoverable so that it cannot be reconstructed
The deletion function in most operating systems allows deleted data to be recovered, so instead, a dedicated secure deletion function or application should be used to make data unrecoverable.
9.5 Point Of Interaction (POI) Devices Are Protected From Tampering And Unauthorized Substitution
9.5.1 POI devices that capture payment card data via direct physical interaction with the payment card form factor are protected from tampering and unauthorized substitution, including the following: • Maintaining a list of POI devices • Periodically inspecting POI devices to look for tampering or unauthorized substitution • Training personnel to be aware of suspicious behavior and to report tampering or unauthorized substitution of devices
Criminals attempt to steal payment card data by stealing and/or manipulating card-reading devices and terminals. Criminals will try to steal devices so they can learn how to break into them, and they often try to replace legitimate devices with fraudulent devices that send them payment card data every time a card is entered.
They will also try to add “skimming” components to the outside of devices, which are designed to capture payment card data before it enters the device for example, by attaching an additional card reader on top of the legitimate card reader so that the payment card data is captured twice: once by the criminal’s component and then by the device’s legitimate component. In this way, transactions may still be completed without interruption while the criminal is “skimming” the payment card data during the process.
9.5.1.1 An up-to-date list of POI devices is maintained, including: • Make and model of the device • Location of device • Device serial number or other methods of unique identification
The method for maintaining a list of devices may be automated (for example, a device-management system) or manual (for example, documented in electronic or paper records). For on-the-road devices, the location may include the name of the personnel to whom the device is assigned.
9.5.1.2 POI device surfaces are periodically inspected to detect tampering and unauthorized substitution
Methods for periodic inspection include checking the serial number or other device characteristics and comparing the information to the list of POI devices to verify the device has not been swapped with a fraudulent device.
9.5.1.2.1 The frequency of periodic POI device inspections and the type of inspections performed is defined in the entity’s targeted risk analysis
The frequency of inspections will depend on factors such as the location of a device and whether the device is attended or unattended. For example, devices left in public areas without supervision by the organization’s personnel might have more frequent inspections than devices kept in secure areas or supervised when accessible to the public. In addition, many POI vendors include guidance in their user documentation about how often POI devices should be checked, and for what entities should consult their vendors’ documentation and incorporate those recommendations into their periodic inspections.
9.5.1.3 Training is provided for personnel in POI environments to be aware of attempted tampering or replacement of POI devices, and includes: • Verifying the identity of any third-party persons claiming to be repair or maintenance personnel, before granting them access to modify or troubleshoot devices • Procedures to ensure devices are not installed, replaced, or returned without verification • Being aware of suspicious behavior around devices • Reporting suspicious behavior and indications of device tampering or substitution to appropriate personnel
Personnel training should include being alert to and questioning anyone who shows up to do POI maintenance to ensure they are authorized and have a valid work order, including any agents, maintenance or repair personnel, technicians, service providers, or other third parties. All third parties requesting access to devices should always be verified before being provided access for example, by checking with management or phoning the POI maintenance company, such as the vendor or acquirer, for verification. Many criminals will try to fool personnel by dressing for the part (for example, carrying toolboxes and dressed in work apparel), and could also be knowledgeable about locations of devices, so personnel should be trained to always follow procedures.
Another trick that criminals use is to send a “new” POI device with instructions for swapping it with a legitimate device and “returning” the legitimate device. The criminals may even provide return postage to their specified address. Therefore, personnel should always verify with their manager or supplier that the device is legitimate and came from a trusted source before installing it or using it for business.
Let’s Understand With An Example
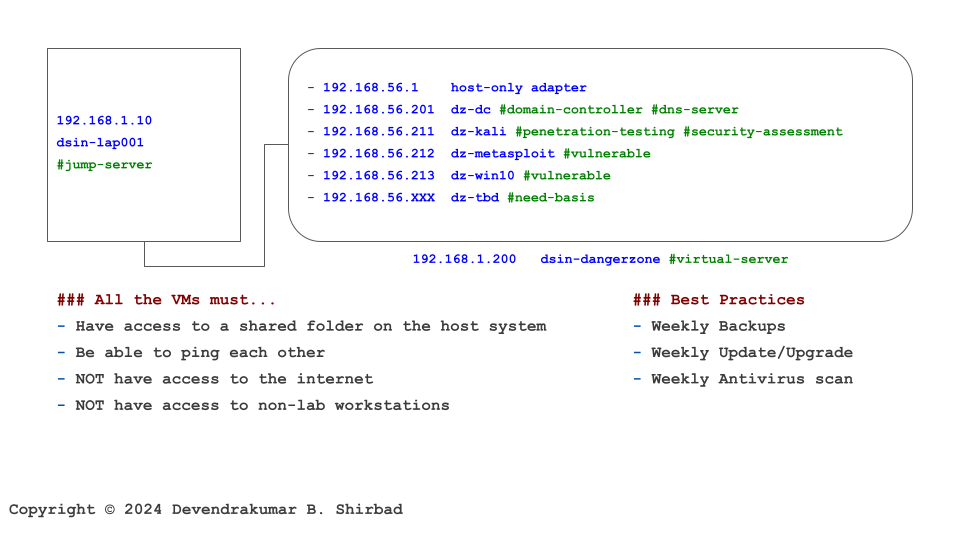
This image is borrowed from the Cybersecurity Labs. Assume it represents your work environment and cardholder data is sitting on the server dz-win10.
Requirement 9.1
It’s all about defining policies and procedures. Then, allocate the responsibilities.
Requirement 9.2
Ideally, dsin-dangerzone should be placed in a marked restricted area with physical locks and monitoring. The gateways, networking/communications hardware etc should be locked.
Requirement 9.3
A clear segregation between employees and visitors with tags can help visually identify them. Then, their identity can be verified/reverified with badges as and when needed. System and Network Admins should be allowed inside the marked restricted area.
Requirement 9.4
All media including hard-copy materials, with cardholder data, should be destroyed when no longer needed. They should be cross-cut shredded, incinerated, or pulped to make recovery difficult. The same applies to physical/virtual disks at dsin-dangerzone. The bottom line is, that cardholder data is rendered unrecoverable when no longer needed by business and legal requirements.
Requirement 9.5
Our example doesn’t include POI device. But assume if we do, it should be protected with the same care as we would have protected dsin-dangerzone. It includes periodically inspecting POI devices to look for tampering or unauthorized substitution.