Angry IP Scanner
In this post, we will use Angry IP Scanner, a GUI tool, to scan the ‘dangerzone.local’ network for host discovery.
Introduction
Source: angryip.org
It is a very fast IP address and port scanner.
It can scan IP addresses in any range as well as any their ports. It’s cross-platform and lightweight. Not requiring any installations, it can be freely copied and used anywhere.
It simply pings each IP address to check if it’s alive, then optionally it is resolving its hostname, determines the MAC address, scans ports, etc. The amount of gathered data about each host can be extended with plugins.
It also has additional features, like NetBIOS information (computer name, workgroup name, and currently logged in Windows user), favorite IP address ranges, web server detection, customizable openers, etc.
Scanning results can be saved to CSV, TXT, XML or IP-Port list files. With help of plugins, it can gather any information about scanned IPs. Anybody who can write Java code is able to write plugins and extend functionality of it.
In order to increase scanning speed, it uses multithreaded approach: a separate scanning thread is created for each scanned IP address. The full source code is available, see the download page.
License
It is free and open-source software, so use it at your own risk. The license is GPLv2.
⚠️ You Have Been Warned
This program is mostly useful for network administrators to monitor and manage their networks.
For more information about IP and port scanning in general, you can see the corresponding article on Wikipedia.
Please note that while theoretically Angry IP Scanner can be used by crackers, in fact it was not intended for doing so, thus the lack of stealth scanning methods. Please do not consider it as a ‘hacktool’ or something similar.
Let’s Get Started!
- Download the IP scanner and OpenJDK.
wget https://aka.ms/download-jdk/microsoft-jdk-21.0.3-windows-x64.msi
wget https://github.com/angryip/ipscan/releases/download/3.9.1/ipscan-win64-3.9.1.exe
- Start all the VMs.
- Copy the OpenJDK and IP scanner to dz-win10 via the shared folder.
- Install OpenJDK.
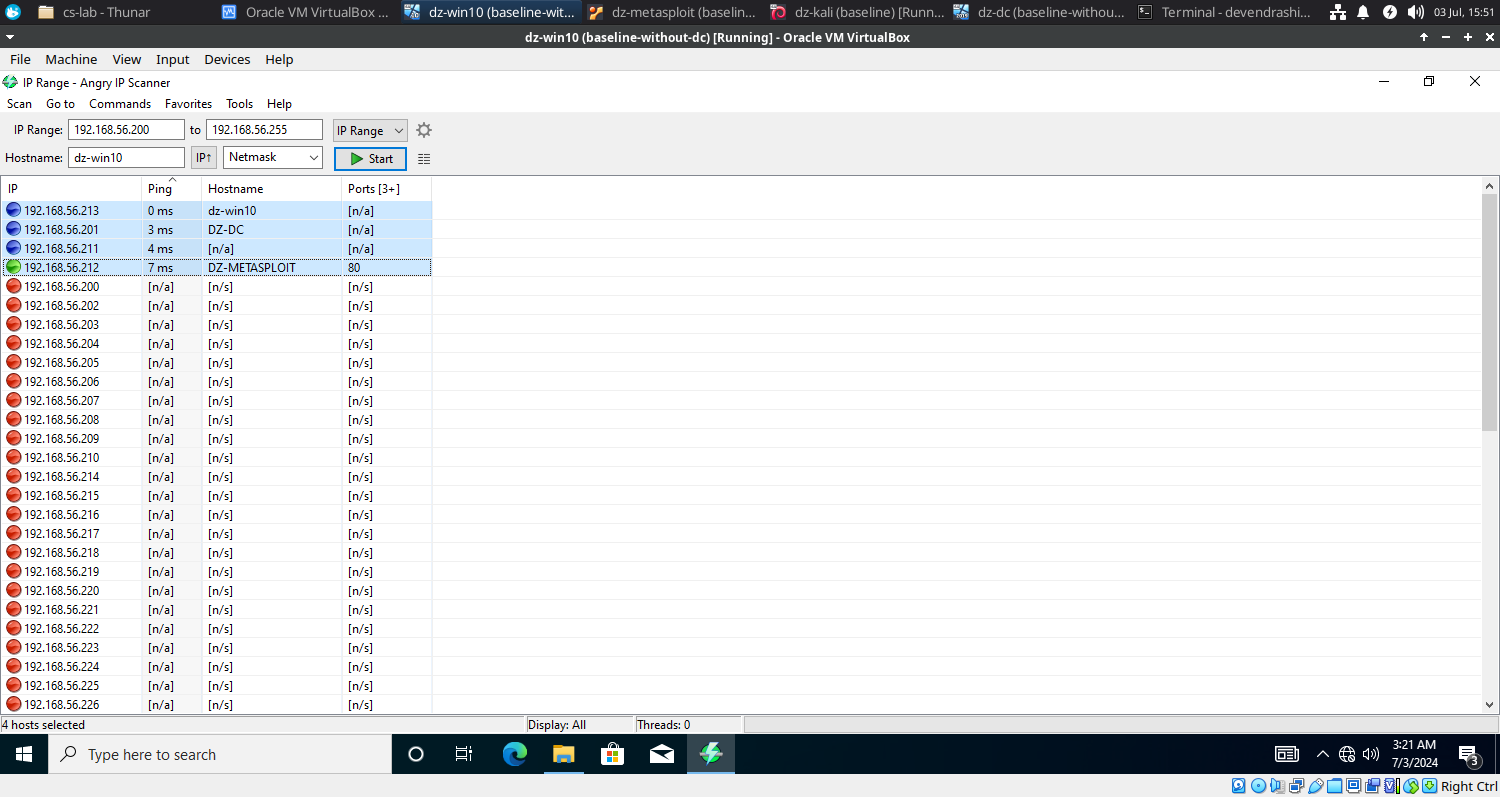
- Launch the IP scanner and scan the network with the IP range 192.168.56.200 – 192.168.56.255.
- Notice the following…
- The scanner successfully identified 4 running systems.
- One of which, dz-metasploit has port 80 (http, web server) open.
- It couldn’t fetch the hostname of dz-kali, which is fine.
- And, it generated the report in a few seconds.
Final Outcome