Cybersecurity Labs: Home
Cybersecurity labs are specialized virtual environments where individuals or organizations can test, analyze, and learn cybersecurity defenses. These labs typically simulate real-world cyber threats and attacks to help users better understand the vulnerabilities of their networks, applications, and devices.
⚠️ You Have Been Warned
- The blog post(s) is written in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
- If the blog post(s) contains any software/program/piece-of-code, it’s distributed under GNU General Public License v3.0.
- It’s NOT a step-by-step guide for newbies. We assume the readers have a basic/advanced level of understanding of operating systems, networking, database/web server administration etc.
Build A Professional Cybersecurity Lab
Architecture
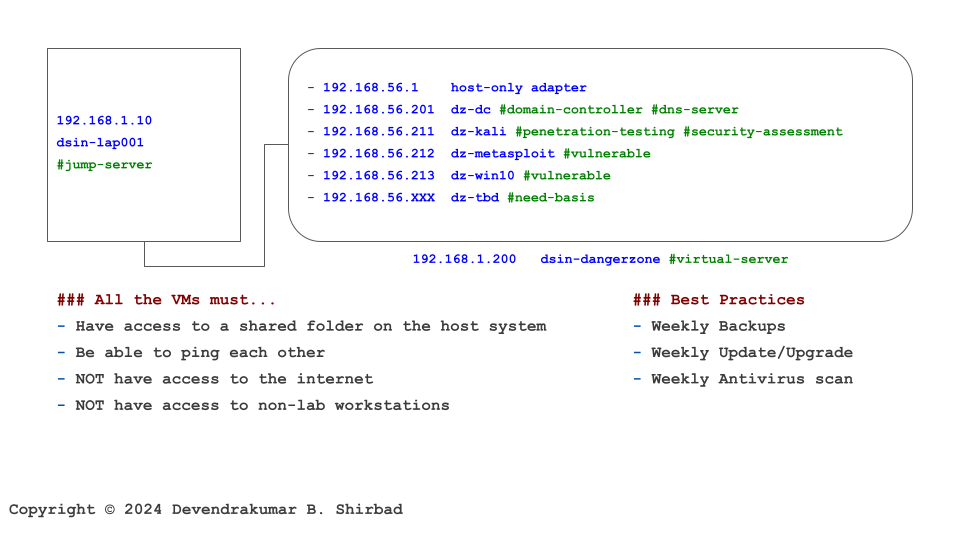
Physical Network and Systems
- 192.168.1.1 dsin-gateway
- 192.168.1.10 dsin-lap001 #jump-server
- 192.168.1.200 dsin-dangerzone #virtual-server
Virtual Network and Systems
- Minimal
- 192.168.56.1 host-only adapter
- 192.168.56.201 dz-dc #domain-controller #dns-server
- 192.168.56.211 dz-kali #penetration-testing #security-assessment
- 192.168.56.212 dz-metasploit #vulnerable
- 192.168.56.213 dz-win10 #vulnerable
- Optional
- 192.168.56.214 dz-owasp #vulnerable
Cost
Reality

So why did we share this picture? The short answer is “to set the expectations right”. You don’t need a fancy-looking setup. If you have not noticed yet, there’s a desktop, a laptop, and a small office local area network with a router (SOHO). That’s good enough to start.
Quality Control
- All the VMs must…
- Have access to a shared folder on the host system
- Be able to ping each other
- NOT have access to the internet
- NOT have access to non-lab workstations
- All the VMs should (optional)…
- Be part of the domain
- Best Practices
- Weekly Backups
- Weekly Update/Upgrade
- Weekly Antivirus scan
Read More: https://devendrashirbad.in/cybersecurity-labs/quality-control/
Safety Rules
We are practically playing with fire here and it’s more likely to catch the fire than you might assume. The quality controls are there to minimize the risks but things may go wrong (horribly wrong). You should follow the safety rules and no harm will come to you.
Cut Your Losses
You should be prepared to contain the malware and minimize the damage if any by wiping out the lab inside out.
- Installed tools
- Disks/Shares
- Virtual Machines
- Virtual Server
- Physical Server
- Jump Server
Valuable/Sensitive Data
You DO NOT store any valuable/sensitive data in the lab.
Restricted Access
Ideally, you should access the lab from the jump-server which is a dedicated system to connect the lab and store no valuable information.
Exceptions
If you must connect the lab from a regular system, make sure to follow the best practices without fail.
Final Outcome
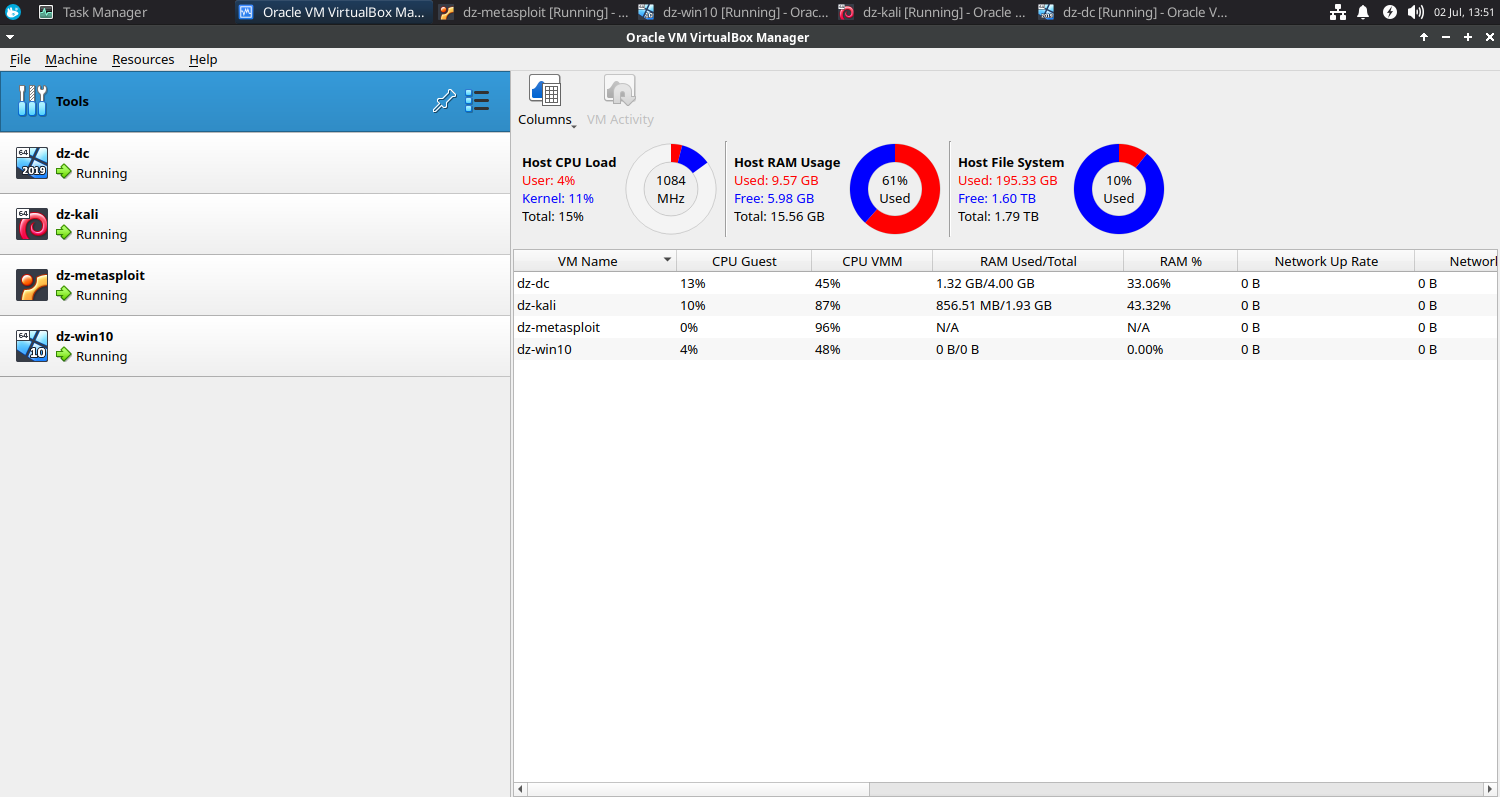
Tools
Enterprise Infrastructure Security
Application And Web Application Security
Work-In-Progress
We are planning to add at least 50 tools/demos in this blog series. Stay informed! Subscribe to our newsletter for the latest updates.