Dz-Owasp #Vulnerable
In this post, we will create a new VM for the Open Worldwide Application Security Project (OWASP) tools e.g. WebGoat, Juice Shop and ZAP. We did not opt for docker because it lacks permanent storage by default. Also, it would be a bit much to manage at least for the beginners.
Virtual Machine Settings
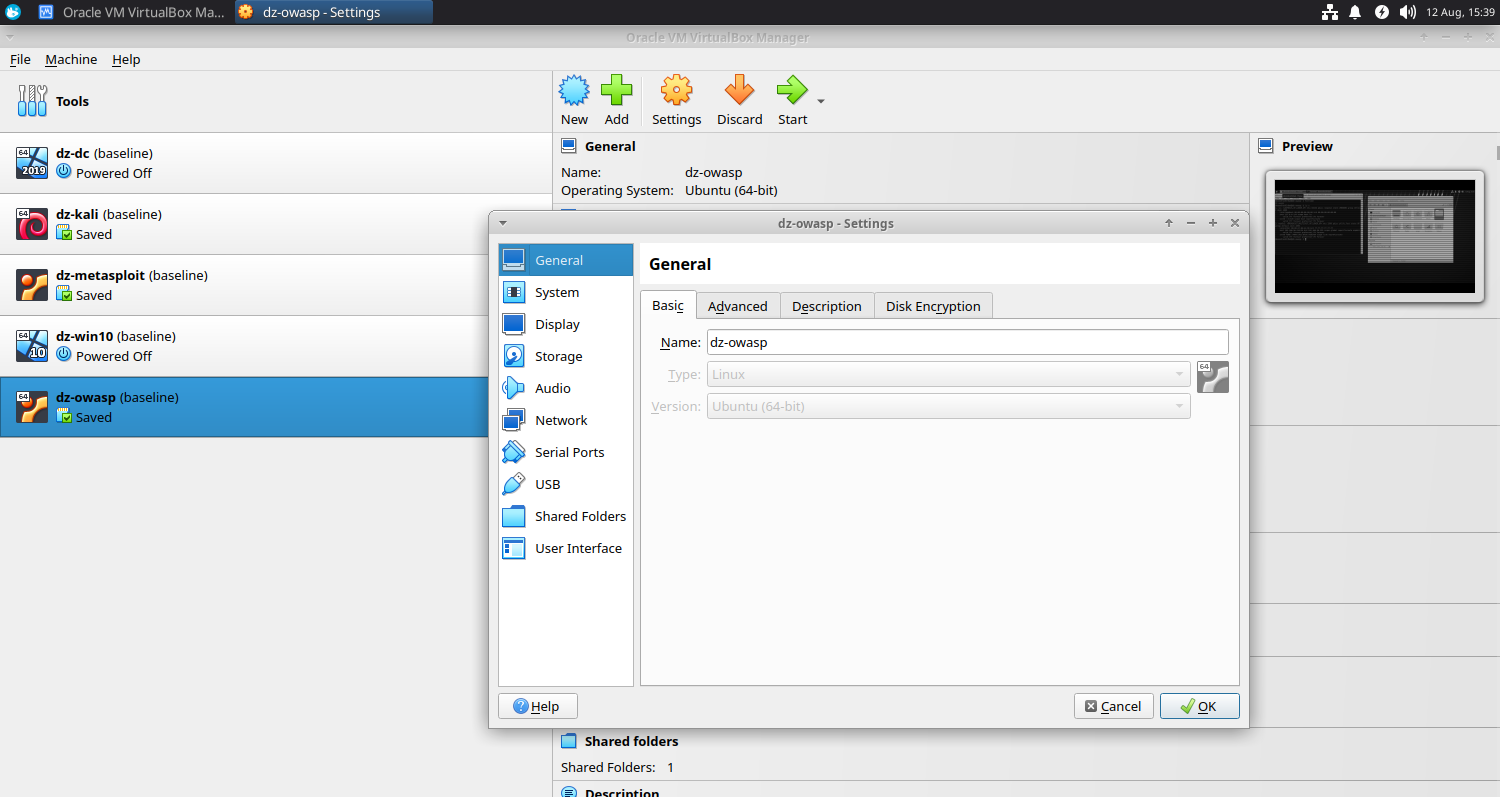
General
- Basic
- Name: dz-owasp
- Type: Linux
- Version: Ubuntu (64 bit)
- Advanced
- Snapshot Folder: /home/devendrashirbad/virtualbox-vms/dz-owasp/Snapshots
- Shared Clipboard: Bidirectional
System
- MotherBoard
- Base Memory: 4096 MB
- Processor
- Processors: 2 CPU
Storage
- Hard Disk: 25 GB (/home/devendrashirbad/virtualbox-vms/dz-owasp/dz-owasp.vdi)
- Optical Drive: /home/devendrashirbad/cs-lab/xubuntu-24.04-desktop-amd64.iso
Network
- Adapter 1
- Host-Only Adapter: vboxnet0
- Adapter 2 (Emergency Only)
- Bridged Adapter: enp3s0
Shared Folder
- Folder Path: /home/devendrashirbad/cs-lab
- Folder Name: cs-lab
- Mount Point: /mnt/cs-lab (auto-mount)
Guest Additions
The Guest Additions are designed to be installed inside a virtual machine after the guest operating system has been installed. They consist of device drivers and system applications that optimize the guest operating system for better performance and usability.
Post Installation
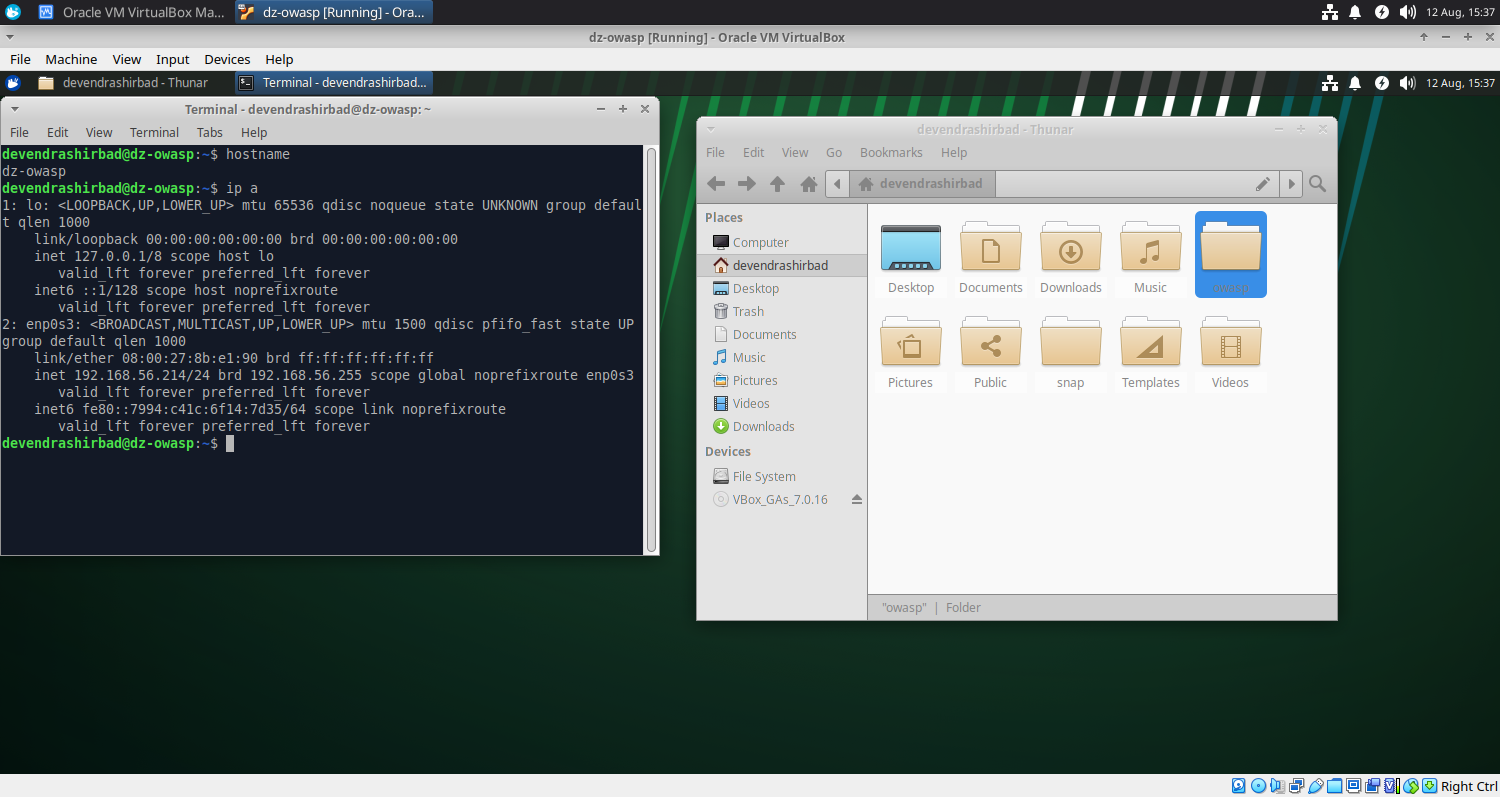
- Rename the hostname to ‘dz-owasp’.
- Change the IP address to ‘192.168.56.214’.
devendrashirbad@dz-owasp:~$ hostname
dz-owasp
devendrashirbad@dz-owasp:~$ ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp0s3: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:8b:e1:90 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.214/24 brd 192.168.56.255 scope global noprefixroute enp0s3
valid_lft forever preferred_lft forever
inet6 fe80::7994:c41c:6f14:7d35/64 scope link noprefixroute
valid_lft forever preferred_lft forever
⚠️ Make It Vulnerable
This system will act as a victim. We will install WebGoat and Juice Shop apps on this system. Then we will use ZAP and other tools for vulnerability assessment and penetration testing.
- WebGoat is a deliberately insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components.
- Juice Shop is probably the most modern and sophisticated insecure web application! It can be used in security trainings, awareness demos, CTFs and as a guinea pig for security tools!
- At its core, ZAP is what is known as a “man-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination.
Read More: Open Worldwide Application Security Project
Final Outcome