Active Directory
In this post, we will configure Active Directory on dz-dc(192.168.56.201) and create a domain ‘dangerzone.local’ with an AD user.
Domain Services
Source: microsoft.com
A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as names, passwords, phone numbers, and so on, and enables other authorized users on the same network to access this information.
Active Directory stores information about objects on the network and makes this information easy for administrators and users to find and use. Active Directory uses a structured data store as the basis for a logical, hierarchical organization of directory information.
This data store, also known as the directory, contains information about Active Directory objects. These objects typically include shared resources such as servers, volumes, printers, and the network user and computer accounts.
Security is integrated with Active Directory through logon authentication and access control to objects in the directory. With a single network logon, administrators can manage directory data and organization throughout their network, and authorized network users can access resources anywhere on the network. Policy-based administration eases the management of even the most complex network.
Network Domains And Domain Controllers
Source: microsoft.com
In a network domain, all applicable Windows Server releases can be configured to be domain controllers. A domain controller is a server that has made its account database available to other machines in a controlled manner.
Because the account database is typically distributed across multiple domain controllers, there can be a mix of different versions of the individual servers. Active Directory defines a functional level, which serves as a version level for the entire directory.
A domain has built-in groups that are defined by Microsoft and created in the domain during installation. For example, built-in groups include the Domain Users, Domain Computers, and Domain Admins groups. By default, the Domain Users group includes all users who are defined in the domain.
A domain controller accepts authentication requests on behalf of the machines that have chosen to trust it and for accounts in its domain.
A domain controller can have peers within the domain, which are other servers that also have been configured to host this account database. Any server that participates in the domain as a domain controller might or might not allow changes; the configuration is a choice of the administrator.
When a change is allowed, the servers replicate the change so that all domain controllers have the same information.
Let’s Get Started!
Dz-Dc(192.168.56.201)
- Open Server Manager > Add Roles and Features > Role-Based or Feature-Based Installation > Select Active Directory Domain Services.
- Promote this server to a domain controller. Add a new forest ‘dangerzone.local’.
Configure this server as the first Active Directory domain controller in a new forest.
The new domain name is "dangerzone.local". This is also the name of the new forest.
The NetBIOS name of the domain: DANGERZONE
Forest Functional Level: Windows Server 2016
Domain Functional Level: Windows Server 2016
Additional Options:
Global catalog: Yes
DNS Server: Yes
Create DNS Delegation: No
Database folder: C:\Windows\NTDS
Log file folder: C:\Windows\NTDS
SYSVOL folder: C:\Windows\SYSVOL
The DNS Server service will be configured on this computer.
This computer will be configured to use this DNS server as its preferred DNS server.
The password of the new domain Administrator will be the same as the password of the local Administrator of this computer.
- Reboot, if prompted.
- Please note that the server is now an Active Directory, Domain Controller and DNS server.
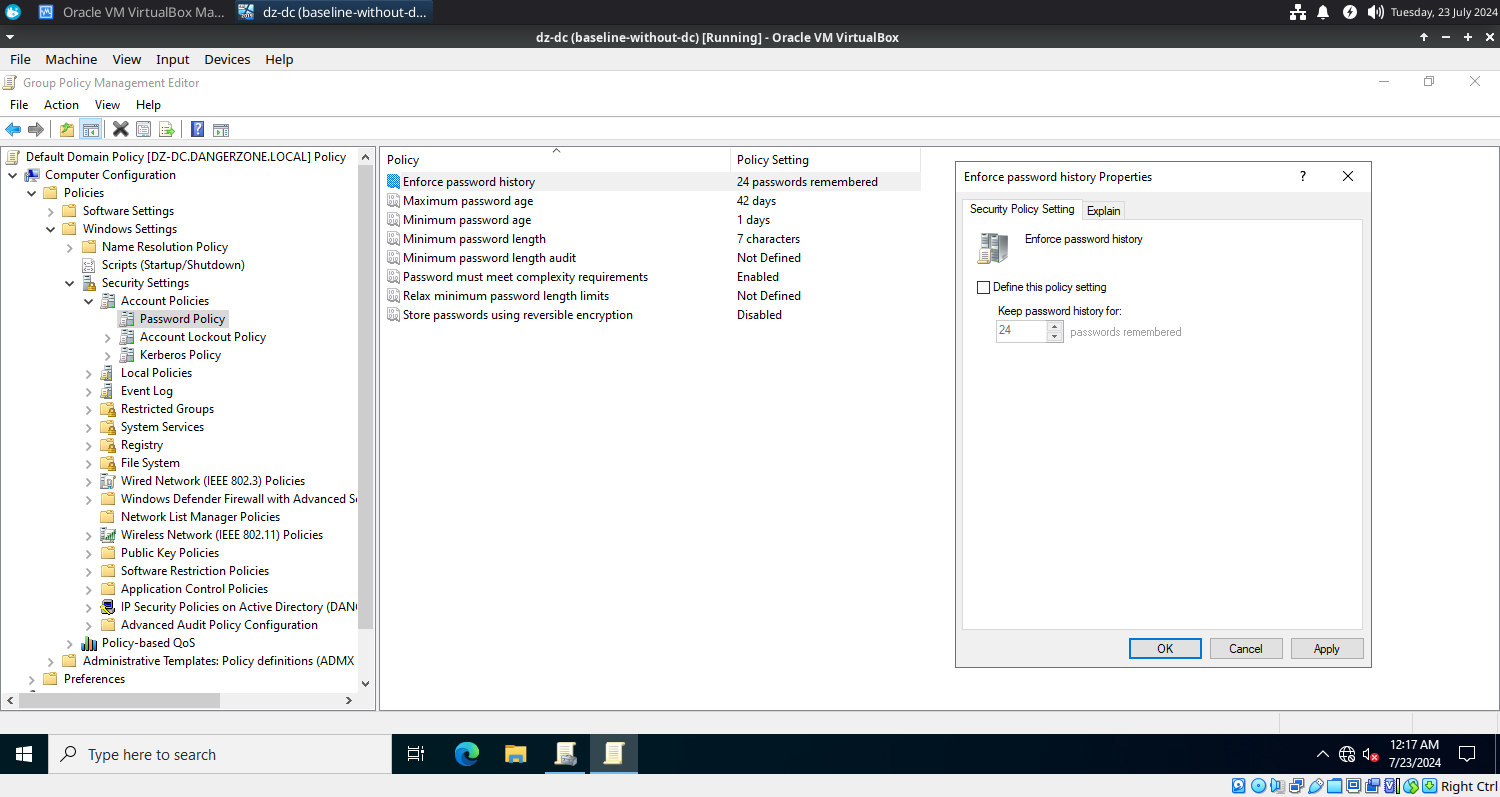
- Under Group Policy Management, Edit the Default Domain Policy and undefine all the password policy. This system will act as a victim so we intentionally disable the security settings and make it vulnerable. You never do it in the PROD systems.
- Under Active Directory Users and Computers, create a new administrator user ‘devendra.shirbad’ (whatever you like).
Copy from: Administrator
Full name: Devendrakumar B. Shirbad
User logon name: devendra.shirbad@dangerzone.local
The password never expires.
Dz-Win10(192.168.56.213)
- Open Network & Internet settings > Change adapter options > properties > Internet Protocol Version 4 > Update the DNS server ‘192.168.56.201’.
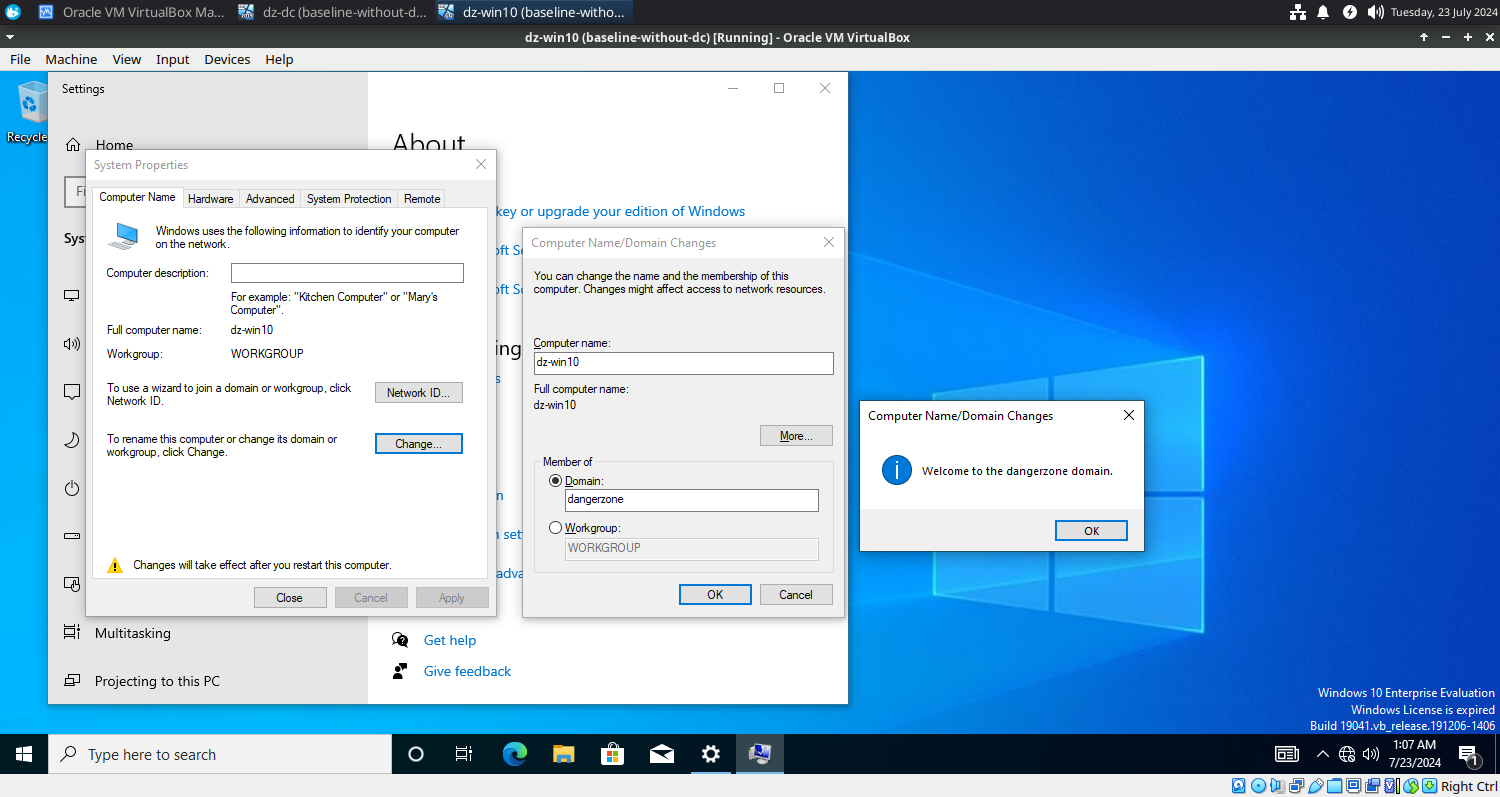
- Open System Properties > Change Domain ‘dangerzone.local’.
- Reboot, if prompted.
Final Outcome
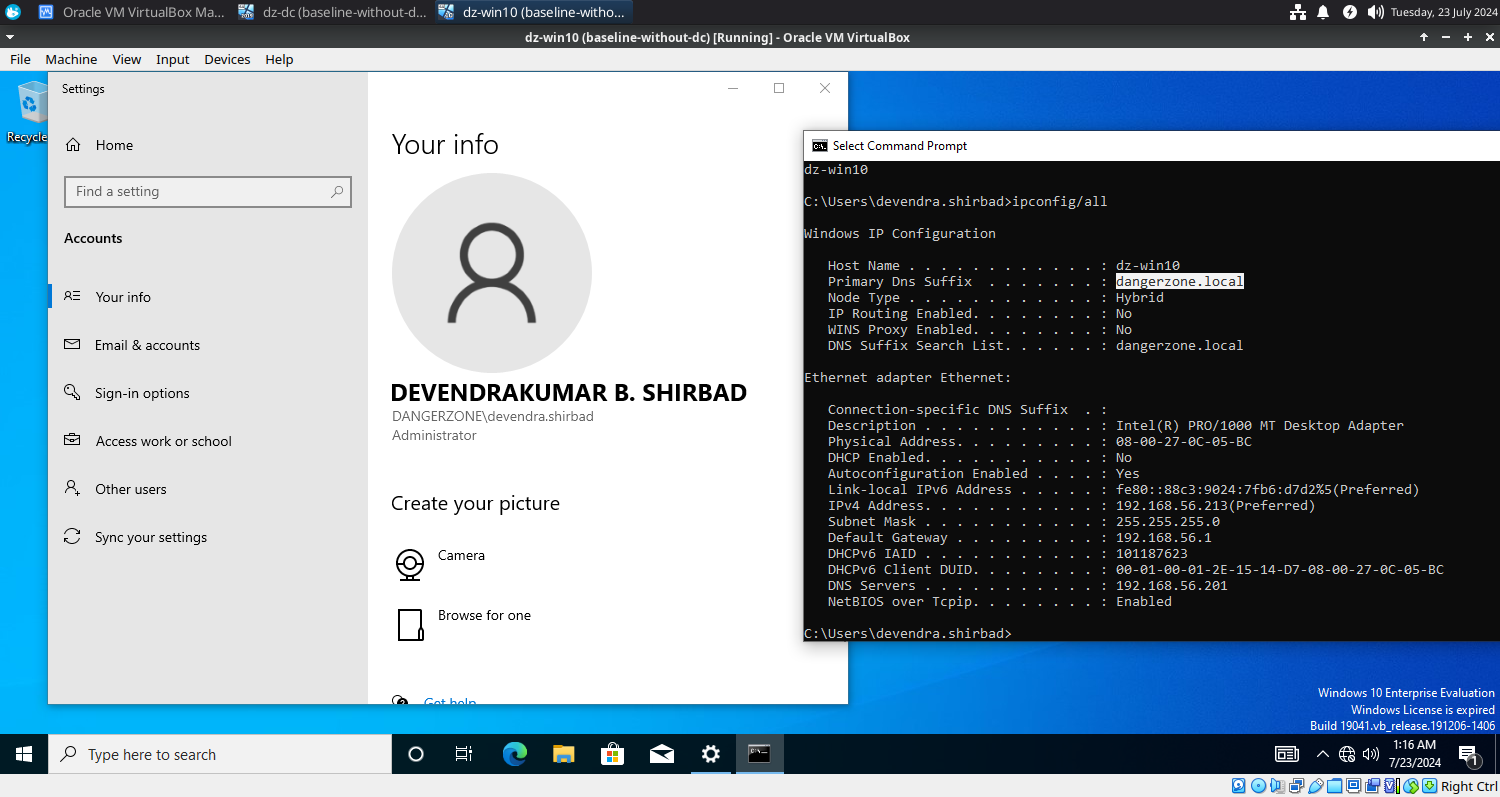
C:\Users\devendra.shirbad>ipconfig/all
Windows IP Configuration
Host Name . . . . . . . . . . . . : dz-win10
Primary Dns Suffix . . . . . . . : dangerzone.local
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : dangerzone.local
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Desktop Adapter
Physical Address. . . . . . . . . : 08-00-27-0C-05-BC
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::88c3:9024:7fb6:d7d2%5(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.56.213(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.56.1
DHCPv6 IAID . . . . . . . . . . . : 101187623
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2E-15-14-D7-08-00-27-0C-05-BC
DNS Servers . . . . . . . . . . . : 192.168.56.201
NetBIOS over Tcpip. . . . . . . . : Enabled