Common Network Tools
In this post, we will use some of the most common tools for network troubleshooting. These tools are shipped with the operating systems.
Net-Tools
Source: launchpad.net
This package includes the important tools for controlling the network subsystem of the Linux kernel. This includes arp, ifconfig, netstat, rarp, nameif and route. Additionally, this package contains utilities relating to particular network hardware types (plipconfig, slattach, mii-tool) and advanced aspects of IP configuration (iptunnel, ipmaddr).
Host
Source: ubuntu.com
host is a simple utility for performing DNS lookups. It is normally used to convert names to IP addresses and vice versa. When no arguments or options are given, host prints a short summary of its command-line arguments and options.
name is the domain name that is to be looked up. It can also be a dotted-decimal IPv4 address or a colon-delimited IPv6 address, in which case host by default performs a reverse lookup for that address. server is an optional argument which is either the name or IP address of the name server that host should query instead of the server or servers listed in /etc/resolv.conf.
Nslookup
Source: ubuntu.com
nslookup is a program to query Internet domain name servers. nslookup has two modes: interactive and non-interactive. Interactive mode allows the user to query name servers for information about various hosts and domains or to print a list of hosts in a domain. Non-interactive mode prints just the name and requested information for a host or domain.
Dig
Source: ubuntu.com
dig is a flexible tool for interrogating DNS name servers. It performs DNS lookups and displays the answers that are returned from the name server(s) that were queried. Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use, and clarity of output. Other lookup tools tend to have less functionality than dig.
Although dig is normally used with command-line arguments, it also has a batch mode of operation for reading lookup requests from a file. A brief summary of its command-line arguments and options is printed when the -h option is given. The BIND 9 implementation of dig allows multiple lookups to be issued from the command line.
Traceroute
Source: wikipedia.org
In computing, traceroute and tracert are diagnostic command-line interface commands for displaying possible routes (paths) and transit delays of packets across an Internet Protocol (IP) network.
The command reports the round-trip times of the packets received from each successive host (remote node) along the route to a destination. The sum of the mean times in each hop is a measure of the total time spent to establish the connection. The command aborts if all (usually three) sent packets are lost more than twice.
Mtr
Source: ubuntu.com
mtr combines the functionality of the traceroute and ping programs in a single network diagnostic tool.
As mtr starts, it investigates the network connection between the host mtr runs on and HOSTNAME by sending packets with purposely low TTLs. It continues to send packets with low TTL, noting the response time of the intervening routers. This allows mtr to print the response percentage and response times of the internet route to HOSTNAME. A sudden increase in packet loss or response time is often an indication of a bad (or simply overloaded) link.
The results are usually reported as round-trip-response times in milliseconds and the percentage of packet loss.
Let’s Get Started
Linux VM
- Run the ifconfig and notice the following
- IP address (inet): 192.168.56.211
- Net Mask (netmask): 255.255.255.0
- Broadcast IP (broadcast): 192.168.56.255
- Ethernet (eth0) and loopback (lo) are network adapters.
┌──(kali㉿dz-kali)-[~]
└─$ ifconfig
eth0: flags=4163 mtu 1500
inet 192.168.56.211 netmask 255.255.255.0 broadcast 192.168.56.255
inet6 fe80::fca5:cdd8:f0f0:3333 prefixlen 64 scopeid 0x20 link
ether 08:00:27:1e:36:4a txqueuelen 1000 (Ethernet)
RX packets 140 bytes 32718 (31.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 167 bytes 28166 (27.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73 mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10 host
loop txqueuelen 1000 (Local Loopback)
RX packets 64 bytes 3240 (3.1 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 64 bytes 3240 (3.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- Run the ip a and notice the following
- IP address (inet): 192.168.56.211
- Net Mask (netmask): /24 (same as 255.255.255.0)
- Broadcast IP (brd): 192.168.56.255
- Ethernet (eth0) and loopback (lo) are network adapters.
┌──(kali㉿dz-kali)-[~]
└─$ ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:1e:36:4a brd ff:ff:ff:ff:ff:ff
inet 192.168.56.211/24 brd 192.168.56.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::fca5:cdd8:f0f0:3333/64 scope link noprefixroute
valid_lft forever preferred_lft forever
- Run the ip route and notice the default gateway 192.168.56.1.
┌──(kali㉿dz-kali)-[~]
└─$ ip route
default via 192.168.56.1 dev eth0 proto static metric 100
192.168.56.0/24 dev eth0 proto kernel scope link src 192.168.56.211 metric 100
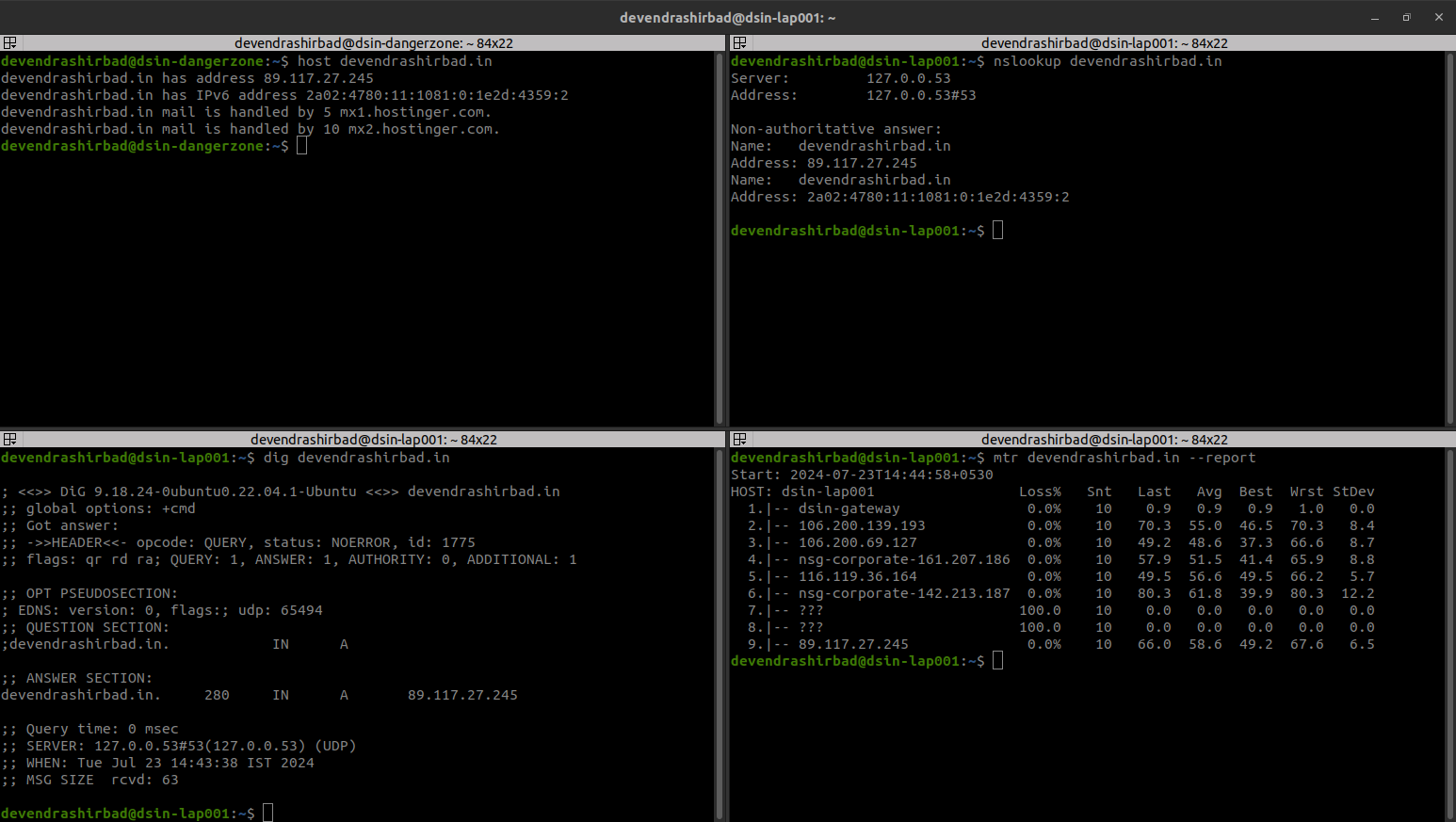
- Run the host command and it returns the minimal information about the domain ‘devendrashirbad.in’.
devendrashirbad@dsin-dangerzone:~$ host devendrashirbad.in
devendrashirbad.in has address 89.117.27.245
devendrashirbad.in has IPv6 address 2a02:4780:11:1081:0:1e2d:4359:2
devendrashirbad.in mail is handled by 5 mx1.hostinger.com.
devendrashirbad.in mail is handled by 10 mx2.hostinger.com.
- Run the host -v command and it returns the detailed information about the domain ‘devendrashirbad.in’.
devendrashirbad@dsin-dangerzone:~$ host -v devendrashirbad.in
Trying "devendrashirbad.in"
;; HEADER opcode: QUERY, status: NOERROR, id: 4874
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;devendrashirbad.in. IN A
;; ANSWER SECTION:
devendrashirbad.in. 207 IN A 89.117.27.245
Received 52 bytes from 127.0.0.53#53 in 0 ms
Trying "devendrashirbad.in"
;; HEADER opcode: QUERY, status: NOERROR, id: 28119
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;devendrashirbad.in. IN AAAA
;; ANSWER SECTION:
devendrashirbad.in. 1708 IN AAAA 2a02:4780:11:1081:0:1e2d:4359:2
Received 64 bytes from 127.0.0.53#53 in 0 ms
Trying "devendrashirbad.in"
;; HEADER opcode: QUERY, status: NOERROR, id: 21487
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;devendrashirbad.in. IN MX
;; ANSWER SECTION:
devendrashirbad.in. 7108 IN MX 5 mx1.hostinger.com.
devendrashirbad.in. 7108 IN MX 10 mx2.hostinger.com.
Received 89 bytes from 127.0.0.53#53 in 0 ms
- Run the nslookup and it returns the minimal information about the domain ‘devendrashirbad.in’.
devendrashirbad@dsin-dangerzone:~$ nslookup devendrashirbad.in
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
Name: devendrashirbad.in
Address: 89.117.27.245
Name: devendrashirbad.in
Address: 2a02:4780:11:1081:0:1e2d:4359:2
- Run the nslookup -query=any and it returns the additional information about the domain ‘devendrashirbad.in’. Try different filters (mx, ns, cname etc).
devendrashirbad@dsin-dangerzone:~$ nslookup -query=any devendrashirbad.in
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
devendrashirbad.in hinfo = "RFC8482" ""
Authoritative answers can be found from:
devendrashirbad@dsin-dangerzone:~$ nslookup -query=mx devendrashirbad.in
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
devendrashirbad.in mail exchanger = 5 mx1.hostinger.com.
devendrashirbad.in mail exchanger = 10 mx2.hostinger.com.
Authoritative answers can be found from:
- Try reverse lookup (i.e. ip address to name translation). It’s amazing.
devendrashirbad@dsin-dangerzone:~$ nslookup dns.google
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
Name: dns.google
Address: 8.8.8.8
Name: dns.google
Address: 8.8.4.4
Name: dns.google
Address: 2001:4860:4860::8844
Name: dns.google
Address: 2001:4860:4860::8888
devendrashirbad@dsin-dangerzone:~$ nslookup 8.8.8.8
8.8.8.8.in-addr.arpa name = dns.google.
Authoritative answers can be found from:
- Run the dig command and it returns the minimal information about the domain ‘devendrashirbad.in’.
devendrashirbad@dsin-dangerzone:~$ dig devendrashirbad.in
; <> DiG 9.18.24-0ubuntu5-Ubuntu <> devendrashirbad.in
;; global options: +cmd
;; Got answer:
;; HEADER opcode: QUERY, status: NOERROR, id: 20108
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;devendrashirbad.in. IN A
;; ANSWER SECTION:
devendrashirbad.in. 300 IN A 89.117.27.245
;; Query time: 235 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Jul 23 14:34:53 IST 2024
;; MSG SIZE rcvd: 63
- Run the dig with ‘any’ option and it returns the additional information about the domain ‘devendrashirbad.in’. Try different filters (mx, ns, cname etc).
devendrashirbad@dsin-dangerzone:~$ dig devendrashirbad.in any
; <> DiG 9.18.24-0ubuntu5-Ubuntu <> devendrashirbad.in any
;; global options: +cmd
;; Got answer:
;; HEADER opcode: QUERY, status: NOERROR, id: 44915
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;devendrashirbad.in. IN ANY
;; ANSWER SECTION:
devendrashirbad.in. 3789 IN HINFO "RFC8482" ""
;; Query time: 86 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (TCP)
;; WHEN: Tue Jul 23 14:36:15 IST 2024
;; MSG SIZE rcvd: 68
devendrashirbad@dsin-dangerzone:~$ dig devendrashirbad.in mx
; <> DiG 9.18.24-0ubuntu5-Ubuntu <> devendrashirbad.in mx
;; global options: +cmd
;; Got answer:
;; HEADER opcode: QUERY, status: NOERROR, id: 41030
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;devendrashirbad.in. IN MX
;; ANSWER SECTION:
devendrashirbad.in. 5613 IN MX 10 mx2.hostinger.com.
devendrashirbad.in. 5613 IN MX 5 mx1.hostinger.com.
;; Query time: 0 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Tue Jul 23 14:36:39 IST 2024
;; MSG SIZE rcvd: 100
- Run the mtr command and notice the hops till the destination.
devendrashirbad@dsin-lap001:~$ mtr devendrashirbad.in --report
Start: 2024-07-23T14:44:58+0530
HOST: dsin-lap001 Loss% Snt Last Avg Best Wrst StDev
1.|-- dsin-gateway 0.0% 10 0.9 0.9 0.9 1.0 0.0
2.|-- 106.200.139.193 0.0% 10 70.3 55.0 46.5 70.3 8.4
3.|-- 106.200.69.127 0.0% 10 49.2 48.6 37.3 66.6 8.7
4.|-- nsg-corporate-161.207.186 0.0% 10 57.9 51.5 41.4 65.9 8.8
5.|-- 116.119.36.164 0.0% 10 49.5 56.6 49.5 66.2 5.7
6.|-- nsg-corporate-142.213.187 0.0% 10 80.3 61.8 39.9 80.3 12.2
7.|-- ??? 100.0 10 0.0 0.0 0.0 0.0 0.0
8.|-- ??? 100.0 10 0.0 0.0 0.0 0.0 0.0
9.|-- 89.117.27.245 0.0% 10 66.0 58.6 49.2 67.6 6.5
Windows VM
- Try tracert on your own. It should show similar output to the mtr command in linux.
C:\Users\devendra.shirbad>tracert dangerzone.local
Tracing route to dangerzone.local [192.168.56.201]
over a maximum of 30 hops:
1 1 ms 1 ms 1 ms DZ-DC [192.168.56.201]
Trace complete.
C:\Users\devendra.shirbad>tracert dz-dc
Tracing route to dz-dc.dangerzone.local [192.168.56.201]
over a maximum of 30 hops:
1 1 ms 1 ms 1 ms DZ-DC [192.168.56.201]
Trace complete.
Final Outcome