Dz-Kali #Penetration-Testing #Security-Assessment
In this post, we will import a pre-built virtual machine of Kali Linux and tweak it. Kali Linux is an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking, and network security assessment.
Kali Tools
The Kali Linux includes security tools, such as Aircrack-ng, Autopsy, Armitage, Burp Suite, BeEF, Cisco Global Exploiter, Ettercap, Foremost, Hydra, Hashcat, John the Ripper, Kismet, Lynis, Maltego, Metasploit framework, Nmap, Nikto, OWASP ZAP, Reverse engineering toolkit, Social engineering tools, Sqlmap, Volatility, VulnHub, Wireshark, WPScan etc. These tools can be used for many purposes, most of which involve exploiting a victim network or application, performing network discovery, or scanning a target IP address.
Virtual Machine Settings
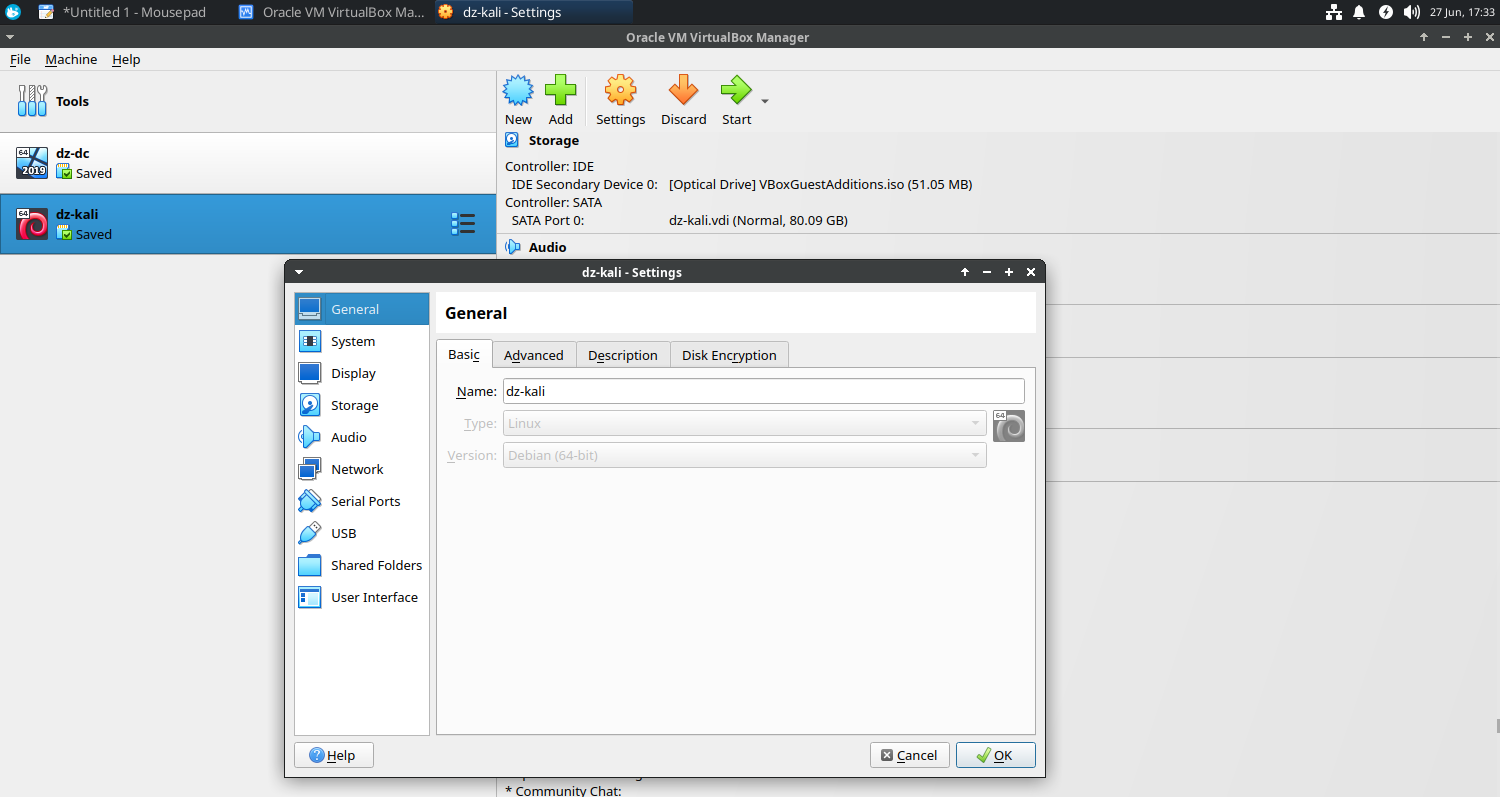
General
- Basic
- Name: dz-kali
- Type: Linux
- Version: Debian (64 bit)
- Advanced
- Snapshot Folder: /home/devendrashirbad/virtualbox-vms/dz-kali/Snapshots
- Shared Clipboard: Bidirectional
System
- MotherBoard
- Base Memory: 2048 MB
- Processor
- Processors: 1 CPU
Storage
- Hard Disk: 80 GB (/home/devendrashirbad/virtualbox-vms/dz-kali/dz-kali.vdi)
- Optical Drive: Empty
Network
- Adapter 1
- Host-Only Adapter: vboxnet0
- Adapter 2 (Emergency Only)
- Bridged Adapter: enp3s0
Shared Folder
- Folder Path: /home/devendrashirbad/cs-lab
- Folder Name: cs-lab
- Mount Point: /mnt/cs-lab (auto-mount)
Guest Additions
The Guest Additions are designed to be installed inside a virtual machine after the guest operating system has been installed. They consist of device drivers and system applications that optimize the guest operating system for better performance and usability.
kali@kali:~$ sudo apt update
kali@kali:~$ sudo apt install -y --reinstall virtualbox-guest-x11
kali@kali:~$ sudo reboot -f
Post Installation
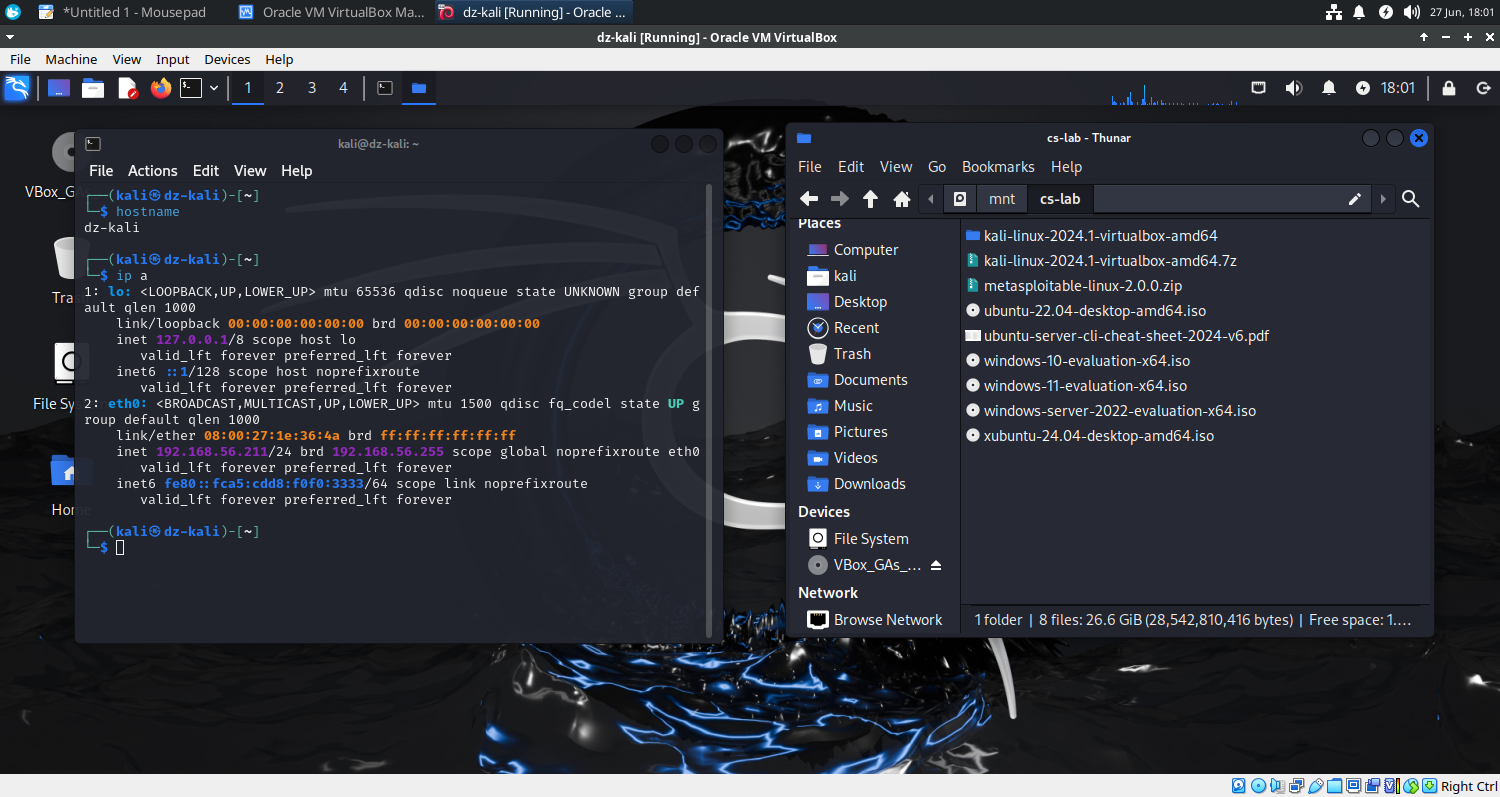
- Rename the hostname to ‘dz-kali’.
- Change the IP address to ‘192.168.56.211’.
┌──(kali㉿dz-kali)-[~]
└─$ ip a
2: eth0: mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:1e:36:4a brd ff:ff:ff:ff:ff:ff
inet 192.168.56.211/24 brd 192.168.56.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::fca5:cdd8:f0f0:3333/64 scope link noprefixroute
valid_lft forever preferred_lft forever
Final Outcome