Nmap: Network Mapper
In this post, we will use the nmap for host discovery, port-scanning, service detection and vulnerability assessment.
Introduction
Source: nmap.org
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X.
In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Features
Flexible
Supports dozens of advanced techniques for mapping out networks filled with IP filters, firewalls, routers, and other obstacles. This includes many port scanning mechanisms (both TCP & UDP), OS detection, version detection, ping sweeps, and more.
Powerful
Nmap has been used to scan huge networks of literally hundreds of thousands of machines.
Portable
Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more.
Easy
While Nmap offers a rich set of advanced features for power users, you can start out as simply as “nmap -v -A targethost”. Both traditional command line and graphical (GUI) versions are available to suit your preference. Binaries are available for those who do not wish to compile Nmap from source.
Free
The primary goals of the Nmap Project is to help make the Internet a little more secure and to provide administrators/auditors/hackers with an advanced tool for exploring their networks. Nmap is available for free download, and also comes with full source code that you may modify and redistribute under the terms of the license.
Well Documented
Significant effort has been put into comprehensive and up-to-date man pages, whitepapers, tutorials, and even a whole book!
Supported
While Nmap comes with no warranty, it is well supported by a vibrant community of developers and users. Most of this interaction occurs on the Nmap mailing lists. Most bug reports and questions should be sent to the nmap-dev list, but only after you read the guidelines. We recommend that all users subscribe to the low-traffic nmap-hackers announcement list.
Useful Options
Host Discovery
-sn: Ping Scan – disable port scan
Port Specification And Scan Order
-p port ranges: Only scan specified ports
Service/Version Detection
-sV: Probe open ports to determine service/version info
Script Scan
sC: equivalent to –script=default
OS Detection
-O: Enable OS detection
Output
-oN/-oX/-oS/-oG file: Output scan in normal, XML, s|rIpt kIddi3, and Grepable format, respectively, to the given filename.
-v: Increase verbosity level (use -vv or more for greater effect)
Miscellaneous
-A: Enable OS detection, version detection, script scanning, and traceroute
Let’s Get Started!
- Download and install it on your favorite OS virtual machine. Otherwise, it’s already pre-installed in the Kali virtual machine.
- Start all the VMs.
- Perform the host discovery in the given network (192.168.56.200 – 192.168.56.220). Notice the message ’21 IP addresses (4 hosts up) scanned in 14.34 seconds’.
┌──(kali㉿dz-kali)-[~]
└─$ nmap -sn 192.168.56.200-220
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 12:31 IST
Nmap scan report for 192.168.56.201
Host is up (0.0027s latency).
Nmap scan report for 192.168.56.211
Host is up (0.00026s latency).
Nmap scan report for 192.168.56.212
Host is up (0.0014s latency).
Nmap scan report for 192.168.56.213
Host is up (0.0023s latency).
Nmap done: 21 IP addresses (4 hosts up) scanned in 14.34 seconds
- Perform the port scan on the specified list (port range 0 – 10000) on the given servers. Notice the difference in outputs, based on different VMs. You can guess the function of the VM based on the open service ports.
┌──(kali㉿dz-kali)-[~]
└─$ nmap -p0-10000 192.168.56.201 192.168.56.211-213
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 12:38 IST
Nmap scan report for 192.168.56.201
Host is up (0.00048s latency).
Not shown: 9987 closed tcp ports (conn-refused)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5357/tcp open wsdapi
5985/tcp open wsman
9389/tcp open adws
Nmap scan report for 192.168.56.211
Host is up (0.00038s latency).
All 10001 scanned ports on 192.168.56.211 are in ignored states.
Not shown: 10001 closed tcp ports (conn-refused)
Nmap scan report for 192.168.56.212
Host is up (0.00035s latency).
Not shown: 9975 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
3632/tcp open distccd
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
6697/tcp open ircs-u
8009/tcp open ajp13
8180/tcp open unknown
8787/tcp open msgsrvr
Nmap scan report for 192.168.56.213
Host is up (0.0019s latency).
Not shown: 9996 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5040/tcp open unknown
Nmap done: 4 IP addresses (4 hosts up) scanned in 18.35 seconds
- Get details about the services on open ports. Notice that the tool was able to identify the services like DNS, Microsoft Windows RPC, Microsoft Windows Active Directory, OpenSSH, Apache, MySQL, PostgreSQL, Microsoft IIS etc. Now, we know as a hacker, where the meat is 😉
┌──(kali㉿dz-kali)-[~]
└─$ nmap -p0-10000 -sV 192.168.56.201 192.168.56.211-213
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-30 12:46 IST
Strange read error from 192.168.56.201 (104 - 'Connection reset by peer')
Nmap scan report for 192.168.56.201
Host is up (0.00090s latency).
Not shown: 9987 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-30 07:16:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: dangerzone.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: dangerzone.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DZ-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap scan report for 192.168.56.211
Host is up (0.00047s latency).
All 10001 scanned ports on 192.168.56.211 are in ignored states.
Not shown: 10001 closed tcp ports (conn-refused)
Nmap scan report for 192.168.56.212
Host is up (0.00033s latency).
Not shown: 9975 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login?
514/tcp open shell Netkit rshd
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Bash shell (BACKDOOR; root shell)
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
5900/tcp open vnc VNC (protocol 3.3)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
6697/tcp open irc UnrealIRCd (Admin email admin@Metasploitable.LAN)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
8787/tcp open drb Ruby DRb RMI (Ruby 1.8; path /usr/lib/ruby/1.8/drb)
Service Info: Hosts: metasploitable.localdomain, dz-metasploit, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 192.168.56.213
Host is up (0.0013s latency).
Not shown: 9996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 4 IP addresses (4 hosts up) scanned in 200.89 seconds
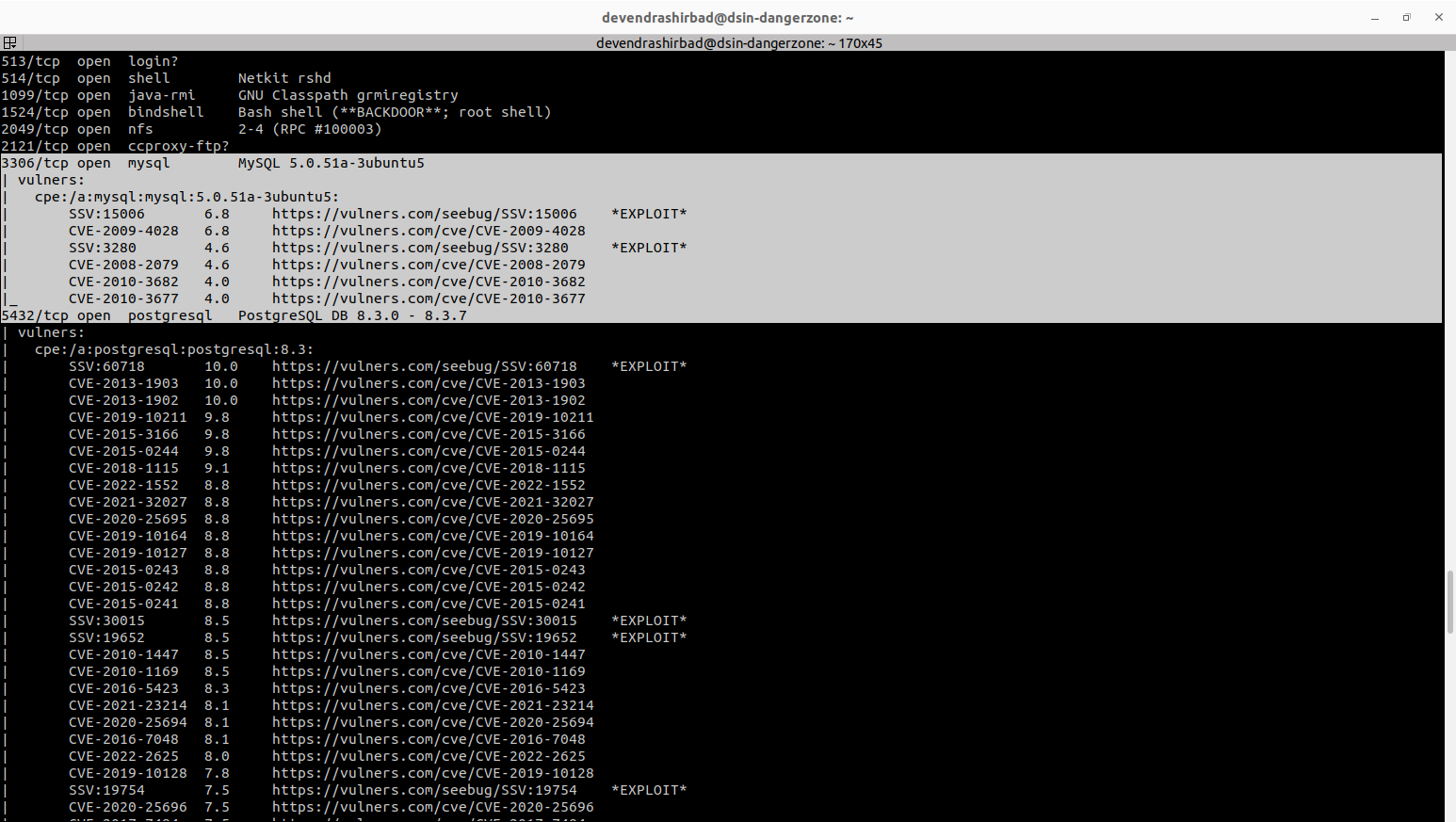
- And, if we can get some information about known vulnerabilities of the servers, life will be really easy 😈. Notice the -oN vulners.out flag to dump the output into a text file. Also, the snippet here contains the vulnerabilities of MySQL 5.0.51a-3ubuntu5 and PostgreSQL DB 8.3.0 – 8.3.7 on dz-metasploit (192.168.56.212). The actual output has ~1100 lines.
# Nmap 7.94SVN scan initiated Tue Jul 30 13:20:52 2024 as: nmap -sV --script vulners -oN vulners.out 192.168.56.201 192.168.56.211-213
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| vulners:
| cpe:/a:mysql:mysql:5.0.51a-3ubuntu5:
| SSV:15006 6.8 https://vulners.com/seebug/SSV:15006 *EXPLOIT*
| CVE-2009-4028 6.8 https://vulners.com/cve/CVE-2009-4028
| SSV:3280 4.6 https://vulners.com/seebug/SSV:3280 *EXPLOIT*
| CVE-2008-2079 4.6 https://vulners.com/cve/CVE-2008-2079
| CVE-2010-3682 4.0 https://vulners.com/cve/CVE-2010-3682
|_ CVE-2010-3677 4.0 https://vulners.com/cve/CVE-2010-3677
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
| vulners:
| cpe:/a:postgresql:postgresql:8.3:
| SSV:60718 10.0 https://vulners.com/seebug/SSV:60718 *EXPLOIT*
| CVE-2013-1903 10.0 https://vulners.com/cve/CVE-2013-1903
| CVE-2013-1902 10.0 https://vulners.com/cve/CVE-2013-1902
| CVE-2019-10211 9.8 https://vulners.com/cve/CVE-2019-10211
| CVE-2015-3166 9.8 https://vulners.com/cve/CVE-2015-3166
| CVE-2015-0244 9.8 https://vulners.com/cve/CVE-2015-0244
| CVE-2018-1115 9.1 https://vulners.com/cve/CVE-2018-1115
| CVE-2022-1552 8.8 https://vulners.com/cve/CVE-2022-1552
| CVE-2021-32027 8.8 https://vulners.com/cve/CVE-2021-32027
| CVE-2020-25695 8.8 https://vulners.com/cve/CVE-2020-25695
| CVE-2019-10164 8.8 https://vulners.com/cve/CVE-2019-10164
| CVE-2019-10127 8.8 https://vulners.com/cve/CVE-2019-10127
| CVE-2015-0243 8.8 https://vulners.com/cve/CVE-2015-0243
| CVE-2015-0242 8.8 https://vulners.com/cve/CVE-2015-0242
| CVE-2015-0241 8.8 https://vulners.com/cve/CVE-2015-0241
| SSV:30015 8.5 https://vulners.com/seebug/SSV:30015 *EXPLOIT*
| SSV:19652 8.5 https://vulners.com/seebug/SSV:19652 *EXPLOIT*
| CVE-2010-1447 8.5 https://vulners.com/cve/CVE-2010-1447
| CVE-2010-1169 8.5 https://vulners.com/cve/CVE-2010-1169
| CVE-2016-5423 8.3 https://vulners.com/cve/CVE-2016-5423
| CVE-2021-23214 8.1 https://vulners.com/cve/CVE-2021-23214
| CVE-2020-25694 8.1 https://vulners.com/cve/CVE-2020-25694
| CVE-2016-7048 8.1 https://vulners.com/cve/CVE-2016-7048
| CVE-2022-2625 8.0 https://vulners.com/cve/CVE-2022-2625
| CVE-2019-10128 7.8 https://vulners.com/cve/CVE-2019-10128
| SSV:19754 7.5 https://vulners.com/seebug/SSV:19754 *EXPLOIT*
| CVE-2020-25696 7.5 https://vulners.com/cve/CVE-2020-25696
| CVE-2017-7484 7.5 https://vulners.com/cve/CVE-2017-7484
| CVE-2016-0773 7.5 https://vulners.com/cve/CVE-2016-0773
| CVE-2016-0768 7.5 https://vulners.com/cve/CVE-2016-0768
| CVE-2015-3167 7.5 https://vulners.com/cve/CVE-2015-3167
| EDB-ID:45184 7.3 https://vulners.com/exploitdb/EDB-ID:45184 *EXPLOIT*
| CVE-2020-14350 7.3 https://vulners.com/cve/CVE-2020-14350
| CVE-2020-10733 7.3 https://vulners.com/cve/CVE-2020-10733
| CVE-2017-14798 7.3 https://vulners.com/cve/CVE-2017-14798
| CVE-2023-2454 7.2 https://vulners.com/cve/CVE-2023-2454
| CVE-2020-14349 7.1 https://vulners.com/cve/CVE-2020-14349
| CVE-2016-5424 7.1 https://vulners.com/cve/CVE-2016-5424
| CVE-2019-10210 7.0 https://vulners.com/cve/CVE-2019-10210
| PACKETSTORM:148884 6.9 https://vulners.com/packetstorm/PACKETSTORM:148884 *EXPLOIT*
| EXPLOITPACK:6F8D33BC4F1C65AE0911D23B5E6EB665 6.9 https://vulners.com/exploitpack/EXPLOITPACK:6F8D33BC4F1C65AE0911D23B5E6EB665 *EXPLOIT*
| 1337DAY-ID-30875 6.9 https://vulners.com/zdt/1337DAY-ID-30875 *EXPLOIT*
| SSV:30152 6.8 https://vulners.com/seebug/SSV:30152 *EXPLOIT*
| CVE-2013-0255 6.8 https://vulners.com/cve/CVE-2013-0255
| CVE-2012-0868 6.8 https://vulners.com/cve/CVE-2012-0868
| CVE-2009-3231 6.8 https://vulners.com/cve/CVE-2009-3231
| SSV:62083 6.5 https://vulners.com/seebug/SSV:62083 *EXPLOIT*
| SSV:62016 6.5 https://vulners.com/seebug/SSV:62016 *EXPLOIT*
| SSV:61543 6.5 https://vulners.com/seebug/SSV:61543 *EXPLOIT*
| SSV:19018 6.5 https://vulners.com/seebug/SSV:19018 *EXPLOIT*
| CVE-2021-3677 6.5 https://vulners.com/cve/CVE-2021-3677
| CVE-2021-32029 6.5 https://vulners.com/cve/CVE-2021-32029
| CVE-2021-32028 6.5 https://vulners.com/cve/CVE-2021-32028
| CVE-2014-0065 6.5 https://vulners.com/cve/CVE-2014-0065
| CVE-2014-0064 6.5 https://vulners.com/cve/CVE-2014-0064
| CVE-2014-0063 6.5 https://vulners.com/cve/CVE-2014-0063
| CVE-2014-0061 6.5 https://vulners.com/cve/CVE-2014-0061
| CVE-2012-0866 6.5 https://vulners.com/cve/CVE-2012-0866
| CVE-2010-4015 6.5 https://vulners.com/cve/CVE-2010-4015
| CVE-2010-0442 6.5 https://vulners.com/cve/CVE-2010-0442
| CVE-2015-5288 6.4 https://vulners.com/cve/CVE-2015-5288
| CVE-2010-3433 6.0 https://vulners.com/cve/CVE-2010-3433
| CVE-2010-1170 6.0 https://vulners.com/cve/CVE-2010-1170
| CVE-2021-23222 5.9 https://vulners.com/cve/CVE-2021-23222
| SSV:19669 5.5 https://vulners.com/seebug/SSV:19669 *EXPLOIT*
| CVE-2010-1975 5.5 https://vulners.com/cve/CVE-2010-1975
| CVE-2023-2455 5.4 https://vulners.com/cve/CVE-2023-2455
| SSV:61546 4.9 https://vulners.com/seebug/SSV:61546 *EXPLOIT*
| SSV:60334 4.9 https://vulners.com/seebug/SSV:60334 *EXPLOIT*
| CVE-2014-0062 4.9 https://vulners.com/cve/CVE-2014-0062
| CVE-2012-3488 4.9 https://vulners.com/cve/CVE-2012-3488
| SSV:61544 4.6 https://vulners.com/seebug/SSV:61544 *EXPLOIT*
| CVE-2014-0067 4.6 https://vulners.com/cve/CVE-2014-0067
| CVE-2021-3393 4.3 https://vulners.com/cve/CVE-2021-3393
| CVE-2021-20229 4.3 https://vulners.com/cve/CVE-2021-20229
| CVE-2015-3165 4.3 https://vulners.com/cve/CVE-2015-3165
| CVE-2014-8161 4.3 https://vulners.com/cve/CVE-2014-8161
| CVE-2012-2143 4.3 https://vulners.com/cve/CVE-2012-2143
| SSV:61547 4.0 https://vulners.com/seebug/SSV:61547 *EXPLOIT*
| SSV:61545 4.0 https://vulners.com/seebug/SSV:61545 *EXPLOIT*
| SSV:60186 4.0 https://vulners.com/seebug/SSV:60186 *EXPLOIT*
| CVE-2014-0066 4.0 https://vulners.com/cve/CVE-2014-0066
| CVE-2014-0060 4.0 https://vulners.com/cve/CVE-2014-0060
| CVE-2012-2655 4.0 https://vulners.com/cve/CVE-2012-2655
| CVE-2009-3229 4.0 https://vulners.com/cve/CVE-2009-3229
| CVE-2022-41862 3.7 https://vulners.com/cve/CVE-2022-41862
| SSV:19322 3.5 https://vulners.com/seebug/SSV:19322 *EXPLOIT*
| PACKETSTORM:127092 3.5 https://vulners.com/packetstorm/PACKETSTORM:127092 *EXPLOIT*
|_ CVE-2010-0733 3.5 https://vulners.com/cve/CVE-2010-0733
Final Outcome