Dz-Metasploit #Vulnerable
In this post, we will create a new VM from a pre-built virtual machine of Metasploitable2 and tweak it. Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools, and practice common penetration testing techniques.
⚠️ You Have Been Warned
This is Metasploitable2 (Linux)
Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools, and practice common penetration testing techniques.
The default login and password is msfadmin:msfadmin.
Never expose this VM to an untrusted network (use NAT or Host-only mode if you have any questions what that means).
To contact the developers, please send email to msfdev@metasploit.com
Virtual Machine Settings
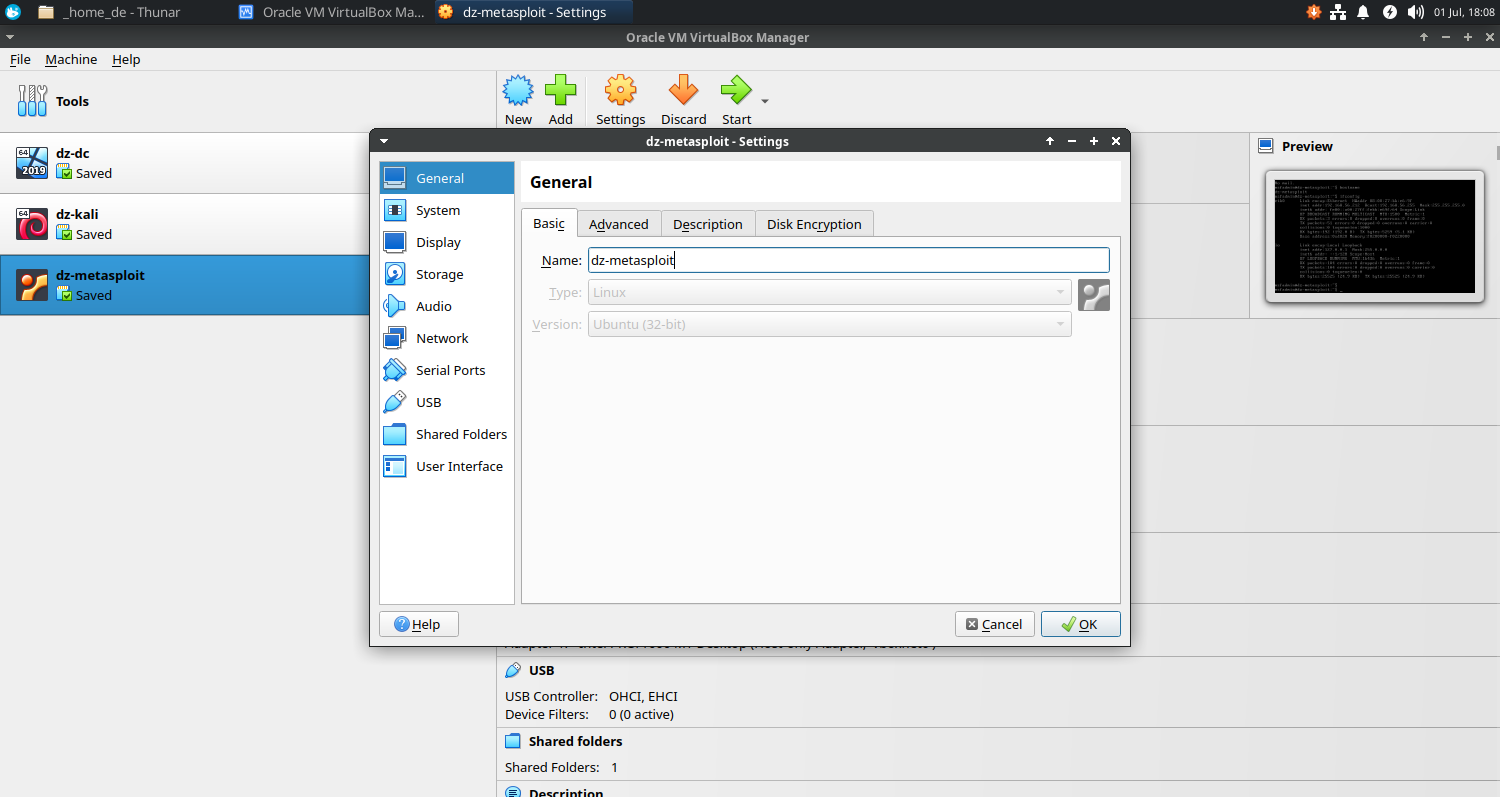
General
- Basic
- Name: dz-metasploit
- Type: Linux
- Version: Ubuntu (32 bit)
- Advanced
- Snapshot Folder: /home/devendrashirbad/virtualbox-vms/dz-metasploit/Snapshots
- Shared Clipboard: Bidirectional
System
- MotherBoard
- Base Memory: 2048 MB
- Processor
- Processors: 1 CPU
Storage
- Hard Disk: 8 GB (/home/devendrashirbad/virtualbox-vms/dz-metasploit/dz-metasploit.vmdk)
- Optical Drive: Empty
Network
- Adapter 1
- Host-Only Adapter: vboxnet0
- Adapter 2 (Emergency Only)
- Bridged Adapter: enp3s0
Shared Folder
- Folder Path: /home/devendrashirbad/cs-lab
- Folder Name: cs-lab
- Mount Point: /mnt/cs-lab (auto-mount)
Guest Additions
I couldn’t find a method to install guest addition components on this pre-built Metasploitable VM. It is based on an old operating system and CLI based. Thus, guest additions are not applicable. Unfortunately, we will not be able to use the clipboard (cut/paste) and shared folder on this VM.
Post Installation
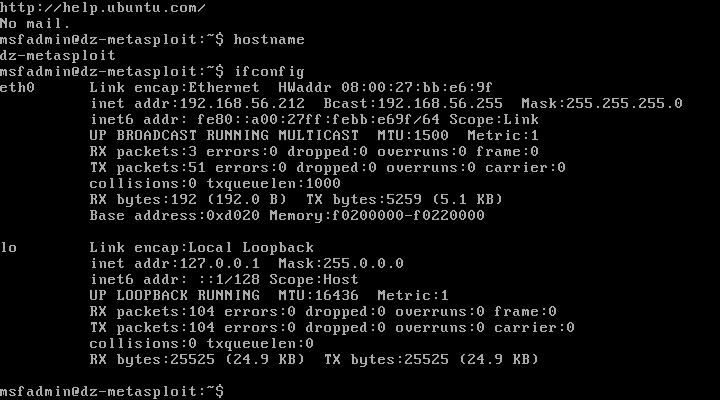
- Rename the hostname to ‘dz-metasploit’.
- Edit ‘/etc/hosts’ and ‘/etc/hostname’
- Change the IP address to ‘192.168.56.212’.
- Edit ‘/etc/network/interfaces’
# auto eth0
iface eth0 inet static
address 192.168.56.212
netmask 255.255.255.0
gateway 192.168.56.1
Final Outcome